Andromeda: The latest Brazilian DTO malware
12 September 2023

Jump to
Introduction
Brazil has been the target of multiple threat actors groups for years, including in the world of mobile banking. In addition to the ongoing activity from threat actors focused on the country's traditional banking ecosystem, increased targeting of more modern financial services technologies has also been observed. This includes the instant payment system developed by the Brazilian Central Bank, known as the Pix Payment System.
In the past, ThreatFabric has discussed several malware families targeting this region and the Pix system in our blog posts about BrasDex and AmexTroll. These malware families offer criminals the ability to perform Device Take Over (DTO), and, in the case of BrasDex, even full Automated Transfer System (ATS) attacks.
Over the course of this year, there have been a multitude of other malware families active in the region (like GoatRAT, PixPIrate, etc.), due in part to the availability of already functional malicious code, as well as development frameworks that bridge the knowledge gap required to develop malware.
As mentioned, these malware families target many of the most prominent banking institutions in Brazil, with techniques that vary from simple overlay and keylogging, to fully-fledged ATS attacks aimed at transferring funds to criminals.
ThreatFabric analysts discovered a new malware family, which we dubbed Andromeda, based on the naming used by the actor who developed the malware. The name comes from the URLs of the C2 servers used to create Remote Access sessions.
DISCLAIMER: In this article we will be reporting our findings about the latest Android Banker, Andromeda. This malware family bears no connection with the older Windows Botnet known as Andromeda, and the identical name is a purely a coincidence.
Andromeda is an in-development banking malware family, created using the B4A development framework, with capabilities including SMS control, PII extraction via overlay, video streaming, and remote access sessions.
In this article, we will discuss the possible attribution of this new banking malware, which has many connections to other existing families, along with technical details about the capabilities of this newly-developed malware family.
B4A Framework
Andromeda is developed using Basic For Android (B4A), a subset of the development framework B4X developed by "Anywhere Software", which covers a wide array of languages and platforms. It allows users to develop applications for platforms without the necessity of knowing the native language, such as Java or, typically in the case of Android, Kotlin. This is achieved by using an intuitive BASIC-like language and simple UI-based designed tools.
This sort of framework bridges the knowledge gap required to develop effective malware, which requires advanced coding skills and a lot of experience. We have previously discussed this development toolkit when talking about AmexTroll and Copybara.
It is important to highlight that B4A and the B4X suite are completely legitimate frameworks and that the developers who created and maintained this project have no control over the misuse of their software.
However, the Brazilian malware community seems to heavily rely on this platform, as confirmed by the number of samples created using this framework that is targeting Brazilian organisations that we are analysing daily.

B4A tends to create Java classes that contain quite a lot of boilerplate code, combined with the fact that Brazilian criminals seem to be willing to re-use and share code with each other. This tends to cause confusion in the InfoSec community, where malware families are continuously mixed up, as mentioned in our article about the repeated misclassification we observed around the Brata malware family.
This is one such reason why such families get grouped together by threat intelligence companies and aggregators.
However, after extensive research and comparisons between the analysed samples and the already-known families using the B4A development toolkit, ThreatFabric has determined that Andromeda is a novel malware family, currently in development.
Andromeda
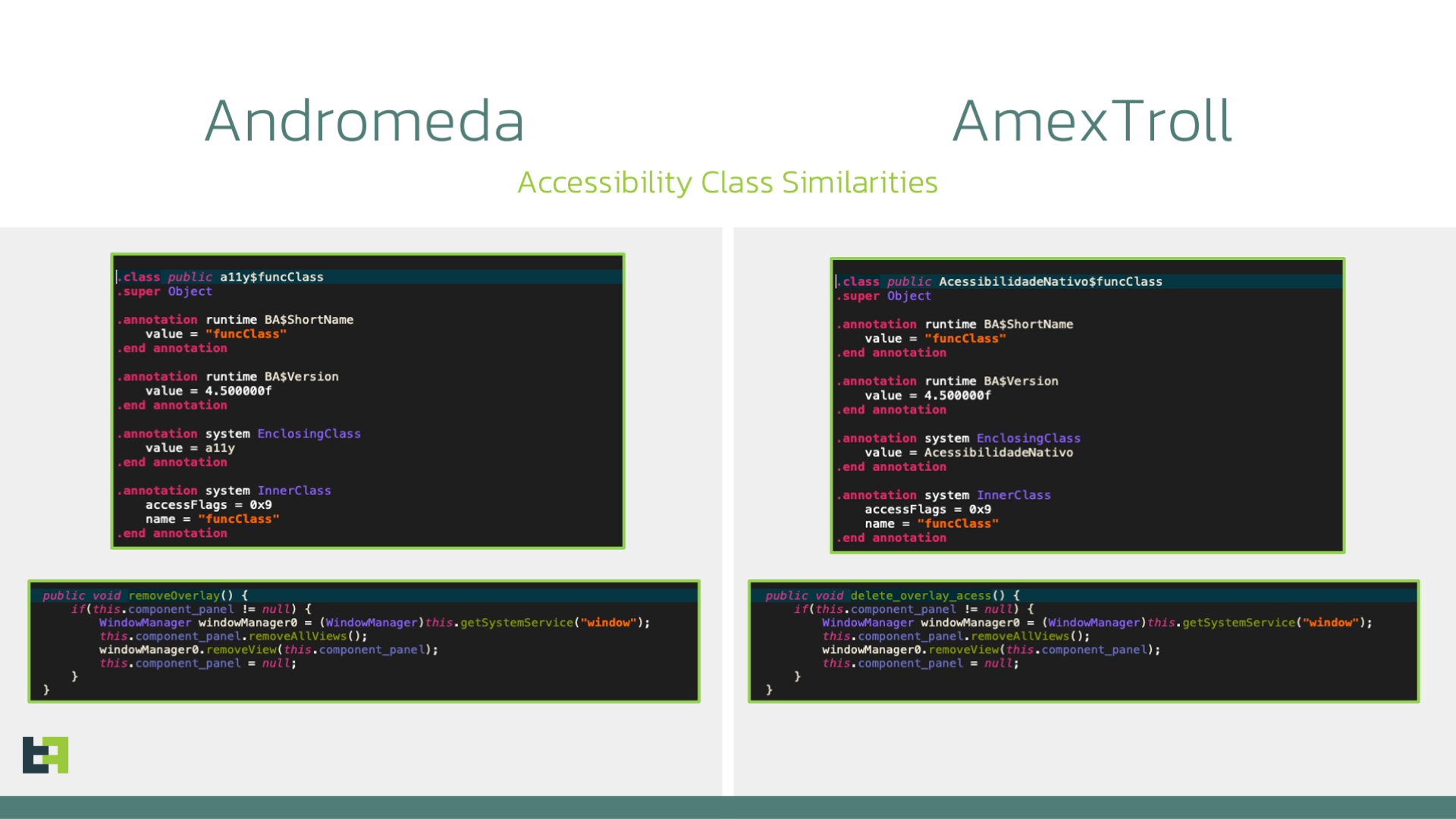
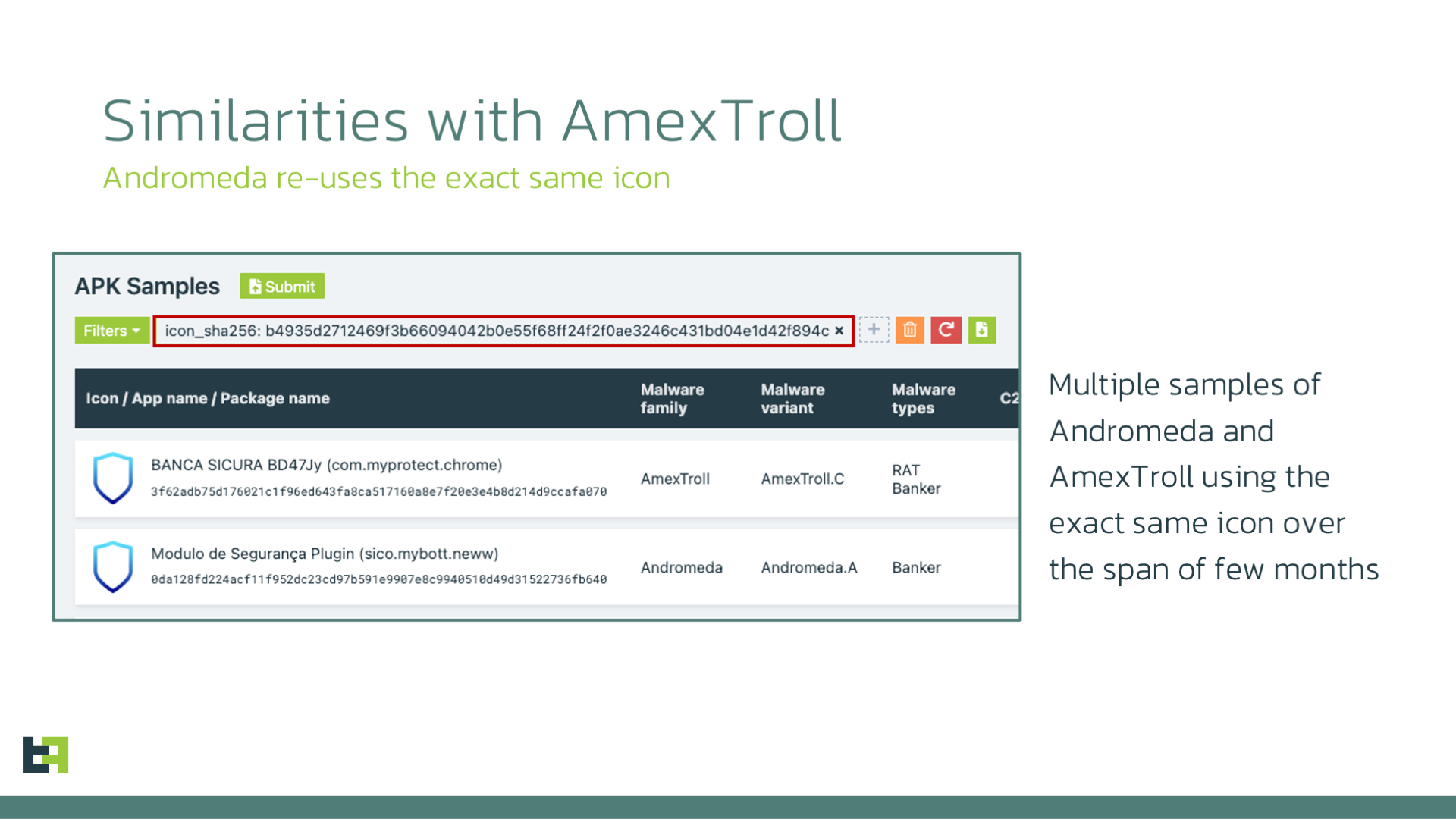
The first time our researchers identified this malware family, they thought they were observing a new variant of the AmexTroll malware family. As we have mentioned, Andromeda samples share the development framework as AmexTroll. In addition, they also use the same exact image file as an icon for the application.
After an initial analysis of the code base of the application, it was obvious that the two malware families were separate entities. The targeted areas differ, as AmexTroll focuses mostly on Italy, with some campaigns targeting Brazil, while Andromeda appears to be solely focusing on Brazil for the time being.
The sheer amount of Java classes and, more importantly, the technologies used to perform capabilities such as remote access, are very different between the two malware families. Most of their commonalities lie in the boilerplate code generated by B4A.
All samples identified and researched were created between March and May 2023. At the time of publishing this article, the servers are offline, probably after noticing the traffic generated by samples that were supposed to be tested.
Capabilities
Andromeda is a malware family that is under development, as some of its features are a work in progress. The malware development shows a clear direction, and it would not be surprising if, in a few weeks or months, it would resurface with additional features and a refined code base.
SMS control / Overlay
Like many other banking malware families, Andromeda features the capability to perform overlay attacks and monitor SMS messages received and sent by the victim. This combination allows criminals to obtain important PIIs, such as web banking or Pix credentials, One-Time Password (OTP) codes, and much more.
At the time of analysis, no overlay was available, confirming once again the testing nature of this malware. Considering the application name, which is consistently some variation of "Modulo de Segurança", translated to "security module" in Portuguese, it is likely that the area of interest of this new malware is going to be Brazil-focused.
It is clear that criminals are testing new features by abusing the overlay mechanism. In these test samples, they defined three specific setups of Layout Parameters for the overlays used by Andromeda. We will discuss the first two, while the third one allows criminals to create overlays that support the introduction of a keyboard:
this.params_no_touchable = new WindowManager.LayoutParams(-1, -1, 0x7F0, 0x2003B8, -3);
this.params_touchable = new WindowManager.LayoutParams(-1, -1, 0x7F0, 0x2003A8, -3);
It is interesting to analyse each value of the LayoutParams to understand what is the meaning of these two objects:
- -1, -1: These are the width and height parameters of the layout, respectively. -1 corresponds to MATCH_PARENT in Android, which means the layout will match the width and height of its parent layout.
- x7F0: This is the type field of the layout parameters, which tells Android what kind of window this is. 0x7F0 corresponds to TYPE_ACCESSIBILITY_OVERLAY. This window type is used by accessibility services to draw overlays on the screen.
- The third parameter is used to set specific flags. Here are the values of the flags:
- FLAG_NOT_FOCUSABLE: The window will not take focus or take it away from another window.
- FLAG_NOT_TOUCH_MODAL: The system will send touch events to the window behind this one if it is not directly targeted by the touch event.
- FLAG_KEEP_SCREEN_ON: The screen should remain on while the window is visible.
- FLAG_LAYOUT_IN_SCREEN: The window should be laid out in such a way as to fit the entire screen, ignoring any constraints from the parent window.
- FLAG_LAYOUT_NO_LIMITS: The window can extend beyond the screen limits.
- FLAG_SECURE: The content of this window can't be captured or copied through normal means, such as screenshots.
- FLAG_NOT_TOUCHABLE: This is the only flag that is different between the two setups, and it stops the window from receiving touch events.
- -3: This is the format parameter, which represents the pixel format. -3 corresponds to PixelFormat.TRANSLUCENT, meaning the window will be translucent, and the content behind it can be seen.
This creates an overlay that does not take focus but takes the whole screen. The option to be "not touchable" allows the criminal to stop the user from interacting with the device, effectively blocking them out.
In addition, there is some experimentation in the source code of Andromeda, which was present only in the more recent samples. If we explore one of the classes named transparentX (with X being a number between 1 and 8), we will see the following screen:
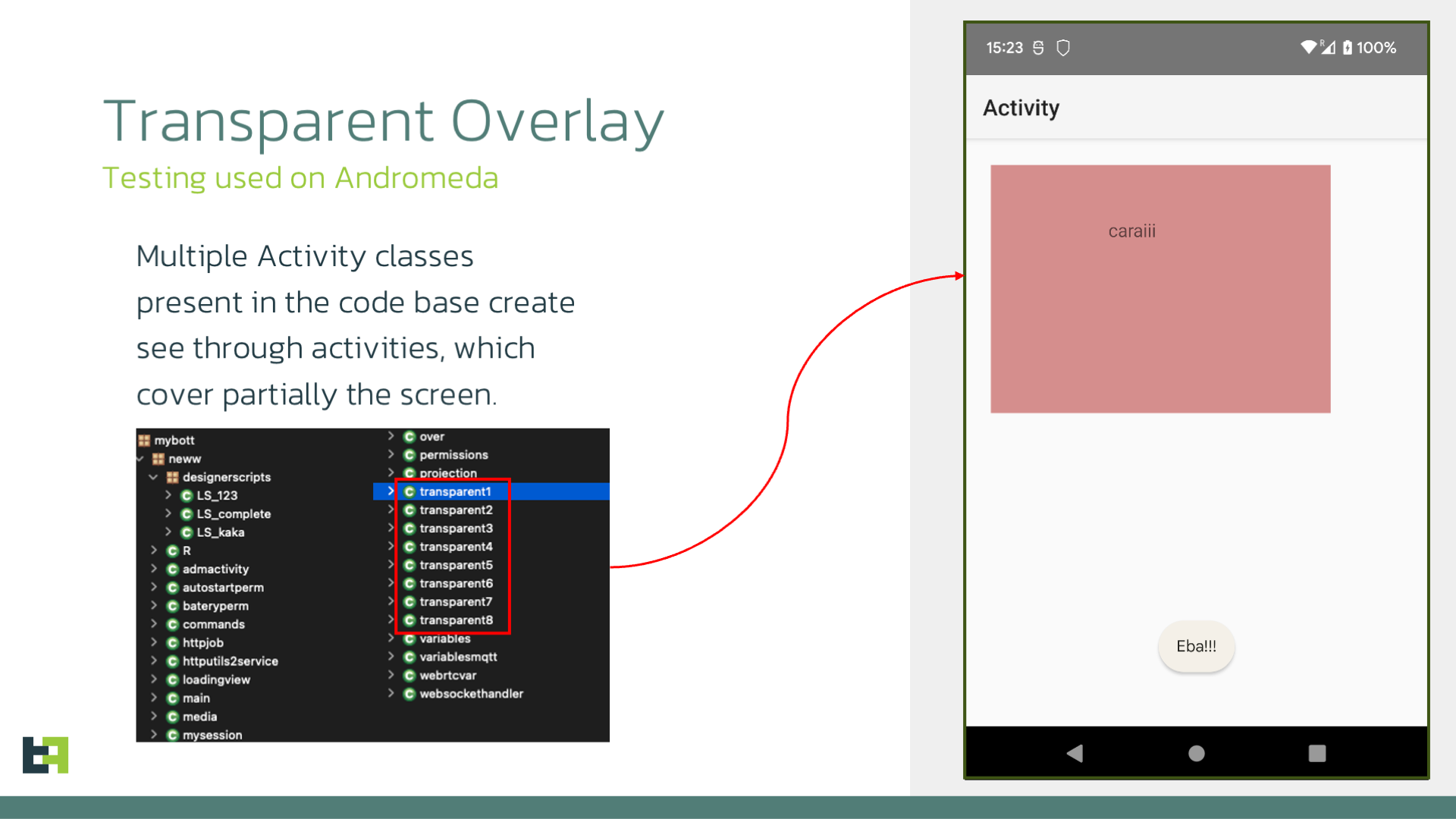
In the screenshot above is a specific layout file, present in the assets in the .bal format, which is a binary file used to save layouts in B4A. The criminals are experimenting with partial overlays, which are based on the class name and might become transparent and displayed on top of other activities of the application.
Andromeda aims at creating an overlay, which could be fully transparent or display some specific URL, together with an additional transparent partial overlay that can be used to hide partial areas of the screen, potentially track inputs where it is positioned, as well as blocking access and touches to such areas.
WebRTC Powered Remote Access
The other main feature of Andromeda is the capability of creating Remote Access sessions to the infected device. This enables criminals to perform Device Take-Over attacks, which are demonstrated to be much harder to detect by Fraud Scoring engines.
The implementation of such sessions is done using a Janus WebRTC server to handle all the communication between the infected device and the C2 server. This choice is unique, as very few malware families have chosen this service to implement their media and data streaming.
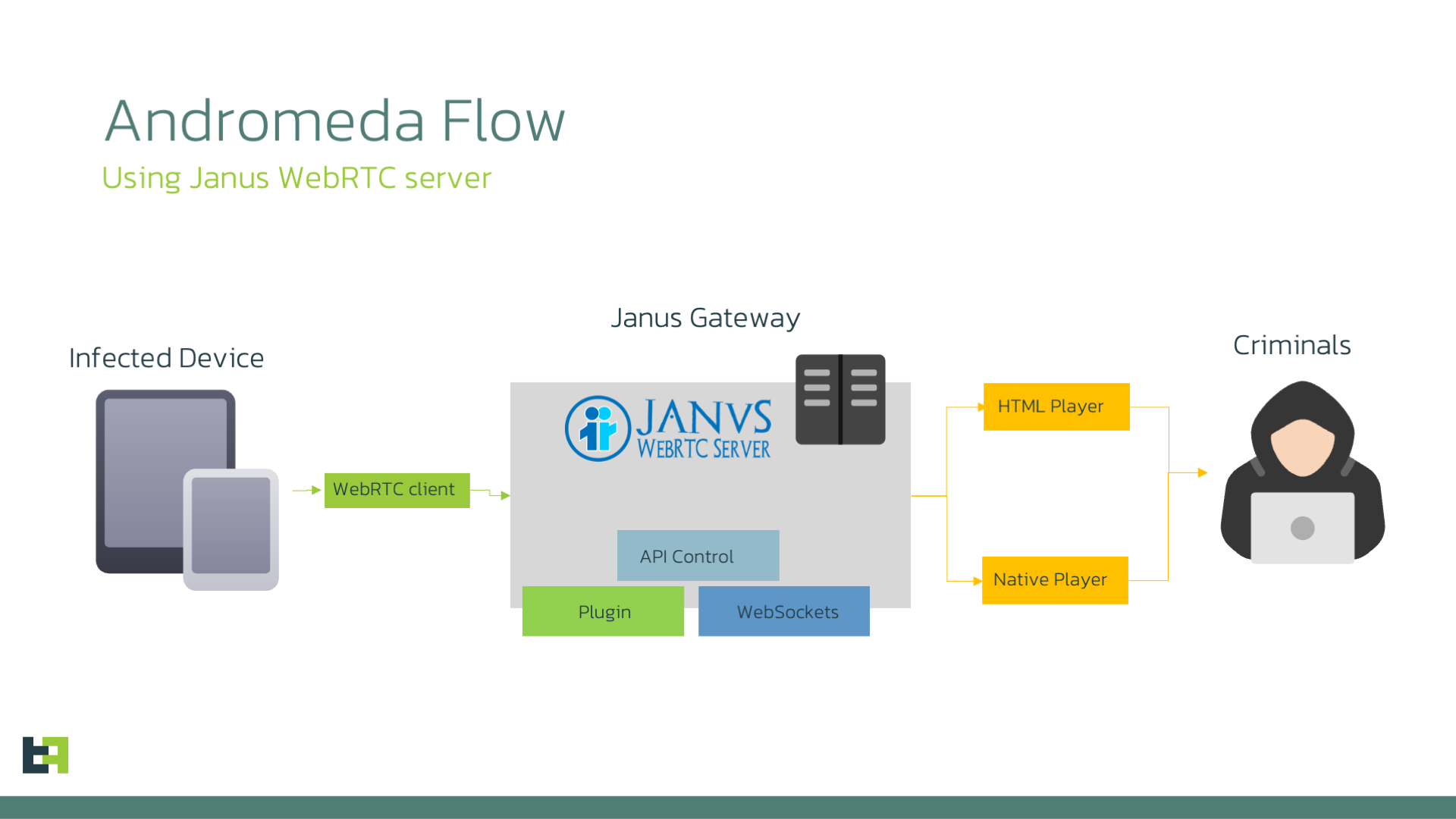
Once again, we want to be sure to highlight that the Janus WebRTC project is a completely legitimate product, and the developers who created this project have no control over the misuse of their software.
The Bot communicates with the server using RESTful API using the following endpoints called with the URL format restapi?decision=<cmd>:
| Command | Description |
| initialize | Register new device |
| attachtextroom | Attaches data only plugin |
| attach streaming | Attaches streaming plugin |
| setuppluginstreat | Setup streaming plugin |
| steupplugintextroom | Setup textroom plugin |
| keepalive | Send keepalive beacon |
| pollingsdp | Poll for session description protocol |
The malware then can perform touches, press buttons, and in general interact with the device's UI using traditional Accessibility Services Actions, triggered by the commands received from the server.
The commands are received over WebSocket communication. Here is the list retrieved from the latest sample:
| Command | Description |
| encoderType | Change AVC encoding for video streaming |
| wipedevice | Format the Device |
| vncQuality | Change the resolution of Remote Streaming |
| openApp | Open other app |
| getsms | Get SMS list |
| getApplications | Get apps list |
| freshSwipe | Perform swipe gesture |
| sendtouch | Send touch event on specified coordinates |
| focusedText | Operate on focused text (delete/copy) |
| vncCustomConfig | Use custom config for codecs |
| vncStandardConfig | Use standard config for codecs |
| unblockTouch | Remove Overlay blocking touch |
| blockTouch | Add Overlay blocking touch |
| onvnc | Enable RAT session |
| deletebot | Delete Itself |
| recents | Press RECENTS |
| home | Press HOME |
| back | Press BACK |
| delOverlay | Delete local overlay |
| freshOverlay | Request fresh overlay (delete old one as well) |
| addOverlay | Request fresh overlay (delete old one as well) |
| permOverlay | Request and accept permission for overlay |
| passOverlay |
Set overlay that allows keyboard inputs
|
It is interesting how actors pay attention to the quality and encoding types used in the WebRTC media streaming, probably to introduce control that could allow them to run the malware on multiple types of devices, as well as connections.
All the code responsible for the remote actions is contained in the class "nw.compass.older". The code used in this class has many connections to the library used by AmexTroll to perform Accessibility actions, even though it adds some functions while missing some others. It is likely that the creators of both families started from the same library, and added the code necessary for their needs.
Possible Attribution
The malware itself is quite interesting, and could potentially be distributed in the future, once it leaves the test phase, to perform DTO fraud in Brazil.
Initially, as we mentioned, we thought that these samples might have been connected with AmexTroll, due to the use of the same exact image as the icon and some similarities in the code base. However, after confirming that there was not enough code shared among the two families, what really sparked our interest was something else.
Here is a brief list of the package names of the discovered samples:
| Package Name |
| admin5.testing.brother |
| app.sickpo.newww |
| sico.mybott.neww |
| sicko.newbot.brabo |
The abundance of the "new" keyword makes it hard to miss, as we mentioned before, Andromeda is a product under development. However, something else caught our attention, the different package names all contain variations around the word "sicko". This is important, as Sicko (aka SickoDevz) is known to be a criminal developer or group active in Brazil, and more specifically the author developing and distributing the GoatRAT malware family.
Currently, GoatRAT, which goes also by the name FantasyMW or CriminalBot, is quite active, and targets multiple financial institutions in Brazil.
The package name alone is not definitive proof of the connection between the authors of these two malware families. ThreatFabric suspects that Andromeda is likely to be the latest project of this actor. In addition to the package name, and the area of origin of the malware author, another clue comes from samples ThreatFabric identified, as belonging to the GoatRAT family.
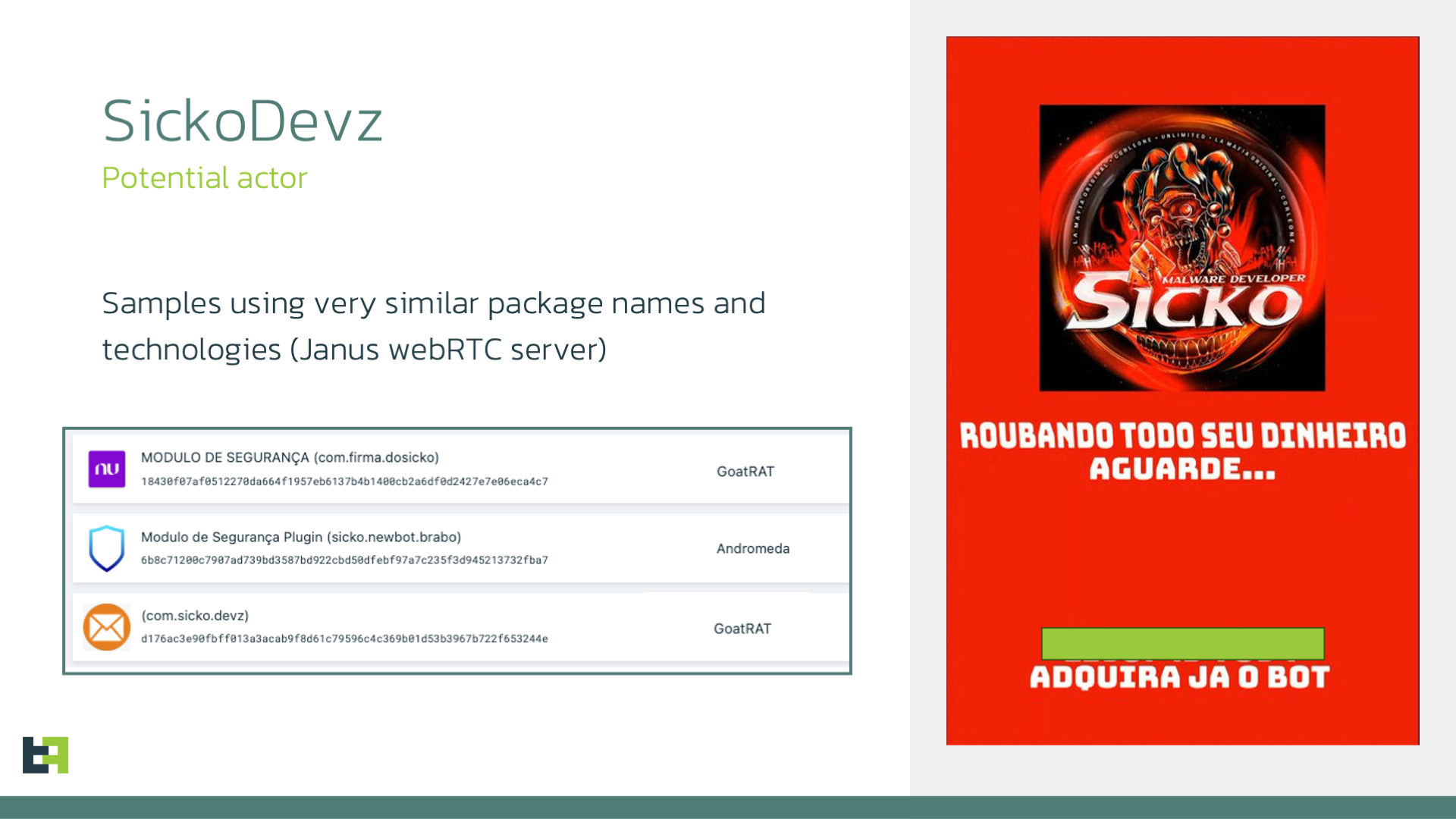
Older samples, which are currently not circulating anymore, presented implementations of Janus Servers to support the WebRTC streaming services, including TextRooms plugins for text exchange between the host and the remote server, and the Streaming plugin for the media streaming. Considering that Janus is a relatively rare option for such services in malware, it strengthens the connection between the development of GoatRAT and the development of Andromeda.
It is worth noting that the Janus experiment for GoatRAT ran from February to March 2023, which is incidentally the month in which the first sample of Andromeda appeared.
One of the online shops connected to the GoatRAT family mentions SickoDevz (the name also present in the package name of the GoatRAT samples using Janus), hinting at the possibility of this being a group of more than a single person. This could also mean that Andromeda is the latest project of one member of SickoDevz, testing out B4A, which we discussed is a platform that is quite popular and successful amongst Brazilian criminals.
For the time being, due to the limited amount of samples connected to the Andromeda family, and the testing nature of such samples, t is possible only to find traces of this possible link. ThreatFabric will continue its monitoring to confirm these theories.
Conclusions
Andromeda is one of the latest examples of Android Banking malware active in Brazil. It is an in-development piece of software, which features the necessary capabilities to exfiltrate PII from victims and perform fraudulent transactions.
It lacks some of the refined options that are present in other malware families, but this will be very likely addressed in the following variants that will appear in the near future. ThreatFabric identified 3 major versions of the malware appearing within just a few weeks of each other, suggesting a current development activity from the criminals behind it. If, as we suspect, this is the work of the SickoDevz group, there is likely no hurry in the development, due to the existence of GoatRAT/FantasyMW/CriminalBot as the currently used Banker.
We suspect that Andromeda will likely receive additional features, present in other malware families developed with B4A like AmexTroll, thanks to the extensive code sharing present among Brazilian criminals.
ThreatFabric will continue closely tracking Andromeda and its potential new developments.
Fraud Risk Suite
ThreatFabric’s Fraud Risk Suite enables safe and frictionless online customer journeys by integrating industry-leading mobile threat intel, behavioural analytics, advanced device fingerprinting, and over 10.000 adaptive fraud indicators. This will give you and your customers peace of mind in an age of ever-changing fraud.
Appendix
Andromeda Samples
| APp name | Package name | SHA256 |
| Modulo de Segurança | admin5.testing.brother | c7f19eae9ff56d59c8d9139fcb29fe93a7bad4b6ed66fe82814271465ebbd852 |
| Modulo de Segurança | app.sickpo.newww | 7091dce65e76ec22a5b3f28edffda92ab7e6691231a003b35c468b7bb6f51826 |
| Modulo de Segurança Plugin | sicko.newbot.brabo | 6b8c71200c7907ad739bd3587bd922cbd50dfebf97a7c235f3d945213732fba7 |
| Modulo de Segurança Plugin | sico.mybott.neww | d264c39860685fefd99417fe43c74916bcb4f1af3a09e9c0bf200a490f99a46e |
Andromeda C2
|
First C2 |
Second C2 (VNC) |
|---|---|
|
5.181.80[.]138:2222 |
- |
|
5.181.80[.]10:4444 |
myvnc.andromedafg9482358dggkj[.]com |
|
5.181.80[.]163:4444 |
myvnc.dumbdroidmyassbig0fsecbniggga[.]com |
|
5.181.80[.]146:2023 |
myvnc.dumbdroidmyassbig0fsecbniggga[.]com |