Anubis II - malware and afterlife
01 March 2019

Jump to
Introduction
Besides being the Egyptian God associated with mummification and afterlife, Anubis is also an Android banking malware that has caused quite some trouble for over 300 financial institutions worldwide since 2017.
Anubis II is the Android banking Trojan created and advertised by an actor with the nickname “maza-in”. This malware family goes beyond the well-known overlay attacks by combining advanced features such as screen streaming, remote file browsing, sound recording, keylogging and even a network proxy, making it an efficient banking malware but also a potential spying tool. Effectively, Anubis can be considered one of the most used Android banking Trojans since late 2017.
As banking malware, Anubis operates by tricking its victims into providing personal and sensitive information such as online banking credentials, banking security codes and even credit card details. Many victims do not realise that the malware application does not pretend to be the bank, it mostly hides as a third-party app and therefore remains under the radar of the average user. Disguises used by Anubis where for example: fake mobile games, fake software updates, fake post/mail apps, fake flash-player apps, fake utility apps, fake browsers and even fake social-network and communication apps.
The malware was rented privately to a limited number of “customers”; criminals willing to use such malware to perform fraud. At the moment of writing, the renting service is supposedly disrupted due to the author being under arrest or having simply vanished with customers’ money, but the malware itself is alive and kicking.
Through this blog post ThreatFabric experts revisit major stages of Anubis’ evolution and explain what changes can be expected on the threat landscape.
Origins: It all started with BankBot
In December 2016 the actor “maza-in” wrote an article named “Android BOT from scratch” in which he shared source code of a new Android banking Trojan capable of sending and intercepting text messages as well as performing overlay attacks to steal credentials.
The article received a lot of attention as it contained sources of both the C2 panel and the Android client (bot), giving actors the tools to create a working banking Trojan with minimum effort. The first malware based on the code from this article was spotted by Dr. Web in Jan 2017 and was dubbed “Android.BankBot.149.origin”. Although being a generic name for banking malware, “BankBot” became the name attributed to all Trojans derived from the shared source code.

Throughout 2017, many actors used Bankbot for their fraudulent operations, but without proper support and updates most abandoned the malware months later. Some however used the source code to build their own malware. Some examples are:
- LokiBot (2017) - the actor behind this malware adapted the original code and introduced the ransomware and proxy capabilities
- Razdel (2017) - a banking malware that primarily target Central European banks, introduced a novel trick to implement overlay attacks
- MysteryBot (2018) - another malware from the same actor that was behind “LokiBot”, introduced a novel keylogging approach and on-device fraud technique
- CometBot (2019) - a copy of the original code with minor modifications, primarily targeting German banks at the moment
Although most actors reusing the original code changed the Trojan into something that suited their respective needs, all of them also kept the original features from the original shared code. The list of these original features is very limited compared to recent banking Trojans but enough to steal personal information from the victims:
- Overlaying: Dynamic - C2 based (possibility to remotely modify the list of targeted application)
- SMS blocking (hiding messages from the victim)
- SMS sending (capability to send messages from the infected device)
- SMS harvesting (possibility to send a copy of all message to the C2 server)
About Anubis
Rise of maza-in
By publishing the aforementioned article, maza-in earned himself a reputation of Android expert on underground forums. He started to share tips and tricks to help other threat actors deal with technical issues and enhance their own malware. Shortly after the initial article, the actor even conducted an interview with Forbes magazine named “I Want To Expose Google’s Mistakes”, stating that he published the malicious code to improve the state of Android security, by showing design flaws in the system that can be easily abused.
He also frequently reviewed each new Android banking Trojan available for renting. In his reviews, he evaluated the technical capabilities and provided his opinion about the actor. Later, a review by maza-in almost became a de facto step to start rental of Android banking malware, as users of forums were asking for the review before they would buy/rent a new Trojan.
Although claiming to have the most noble intentions, maza-in also pursued more nefarious goals. Information from forums shows that at the same time he shared the code of the Trojan in the tutorial article, he was developing a “full” version of the Trojan privately. After some time he started to privately rent it.
The malware was heavily enhanced compared to its original version, adding modern overlaying techniques, device screen recording and streaming, a network proxy feature, keylogging and the ability to steal files from the infected device. maza-in names the malware Anubis and used the following logo in his advertisement of the malware

The list of bot features below shows how much maza-in improved upon the original shared BankBot code to create (the latest version of) Anubis:
- Overlaying: Static (hardcoded in bot)
- Overlaying: Dynamic (C2 based)
- Keylogging
- Contact list collection
- Screen streaming
- Sound recording
- SMS harvesting: SMS forwarding
- SMS blocking
- SMS sending
- Files/pictures collection
- Calls: USSD request making
- Ransomware: Cryptolocker
- Remote actions: Data-wiping
- Remote actions: Back-connect proxy
- Notifications: Push notifications
- C2 Resilience: Twitter/Telegram/Pastebin C2 update channels
In addition to the new features and improvements made, Anubis also has a larger (default) target list. In the Appendix you can find a full list of apps targeted by Anubis (437 applications in total).
Distribution
As a rented Trojan, Anubis was distributed using a wide range of delivery techniques:
- Google Play campaigns: using self-made or rented droppers actors were able to bypass Google Play security mechanisms and spread the Trojan using the official app store, potentially infecting thousands of victims at a time.
- Spam campaigns: using SMS or email, actors sent messages to social engineer the victims with a request to install or update some legitimate application, instead linking to the malware.
- Web-redirection of the victim to a fake landing page containing a request to install or update some legitimate application, instead linking to the malware; using advertisement on websites, hacked sites, traffic exchanges and other black hat SEO methods
It is in the interest of the actors to infect as many devices as possible as it increases the chances to commit fraud successfully. The problem for Play Store users is that even without being social-engineered, due to the increasing number of Google Play malware campaigns, the risk of downloading a dropper mimicking a benign application has increased significantly. Therefore the statement “only download apps from the official app store” is not enough to remain safe from malware.
Recent updates
The rental of Anubis 2 was open from Q4 2017 until February 2019. During Q1 2019, actor maza-in vanished from the threat landscape, leaving existing customers without support and updates. Although exact details about the vanishing of the actor remain unclear at the time of writing, a chain of events confirms that some abnormal activity took place around Anubis and its author.
- On December 13 2018 maza-in announces the release of Anubis 2.5; seemingly only redesigning the backend web interface, while actually stating that he rewrote the whole bot code.
- On January 16 2019 Anubis code is leaked in an underground forum (both backend code and unobfuscated APK).
- On February 14 2019 for the first time an Anubis sample seen targeting Russian banks only is spotted (indicating a new campaign / new operator).
- On February 25 2019 some complaints from Anubis customers appear in underground forums stating that maza-in and Anubis support no longer reply to messages.
- On March 04 2019, the admin of one underground forum states maza-in got arrested. Shortly after this, accounts of maza-in are banned on multiple forums.
- During March 2019, actor Aldesa (who shares a connection with maza-in) creates a post to sell the so-called “Anubis 3” malware on an underground forum. His post gets removed by the admin quite quickly.
We can conclude that the Anubis Trojan is no longer officially rented. However, ThreatFabric experts have observed certain Anubis customers having access to the builder and admin panel, which explains why the operations have not been totally disrupted.
Although it is hard to say why maza-in really vanished, the fact that some code has been leaked combined with recent observations of unobfuscated Anubis samples in the wild, may suggest that the malware will be used by other actors and thus remain active.
What we learned from history
In the past, several other banking Trojans have seen their operations being disrupted and/or source code leaked. It often results in a decrease in the operations and number of samples generated, but most often activity resumes after some quiet time.
There might be some explanations to this such as actors/operators being scared of sudden changes, possibly indicating take-downs or arrests; the time needed to get hands on the right resources and accounts to resume operations; delay between the moment operations stop and leaking of source code; etc… In some cases, the calm after the storm resulted in some new variants appearing on the threat landscape, indicating the delay was probably due to the need for other actors to build their own malware version/variant based on the leaked code.
Marcher
In 2016, the operations of another popular Android banking malware named Marcher were disrupted in a similar way to what happened to Anubis. The actor behind the Marcher Trojan got banned and the renting service was discontinued. The renting model of that Trojan allowed purchase of the APK (bot) builder, therefore a number of Marcher actors obtained the source code of the admin panel and the bot itself.
Some of them resold the sources and some of them used them as a base for their own banking malware; therefore, although operations were disrupted the Trojan remained active for a while and new malware families emerged. Examples of modern families based on Marcher are:
- ExoBot
- Gustuff
- DiseaseBot
- Bubabot
- Neobot
Even now it sometimes happens that some new Marcher-based Trojans appear on the threat-landscape.
The story repeats itself
Looking at actual situation for Anubis, several scenarios are possible:
- Actors having access to relevant resources continue using Anubis in it’s actual state
- Some actor or actor group will step in and will become the new maintainer of Anubis, business starts over
- Actors stop using Anubis and wait for some new banking malware to become available
- Actors having access to relevant resources will start to modify and improve the existing code base to create their own malware
As mentioned before, Anubis itself is based on the Bankbot Trojan, which was made public on purpose. This resulted in the appearance of at least 4 distinctive malware families/variants as shown in the picture hereunder
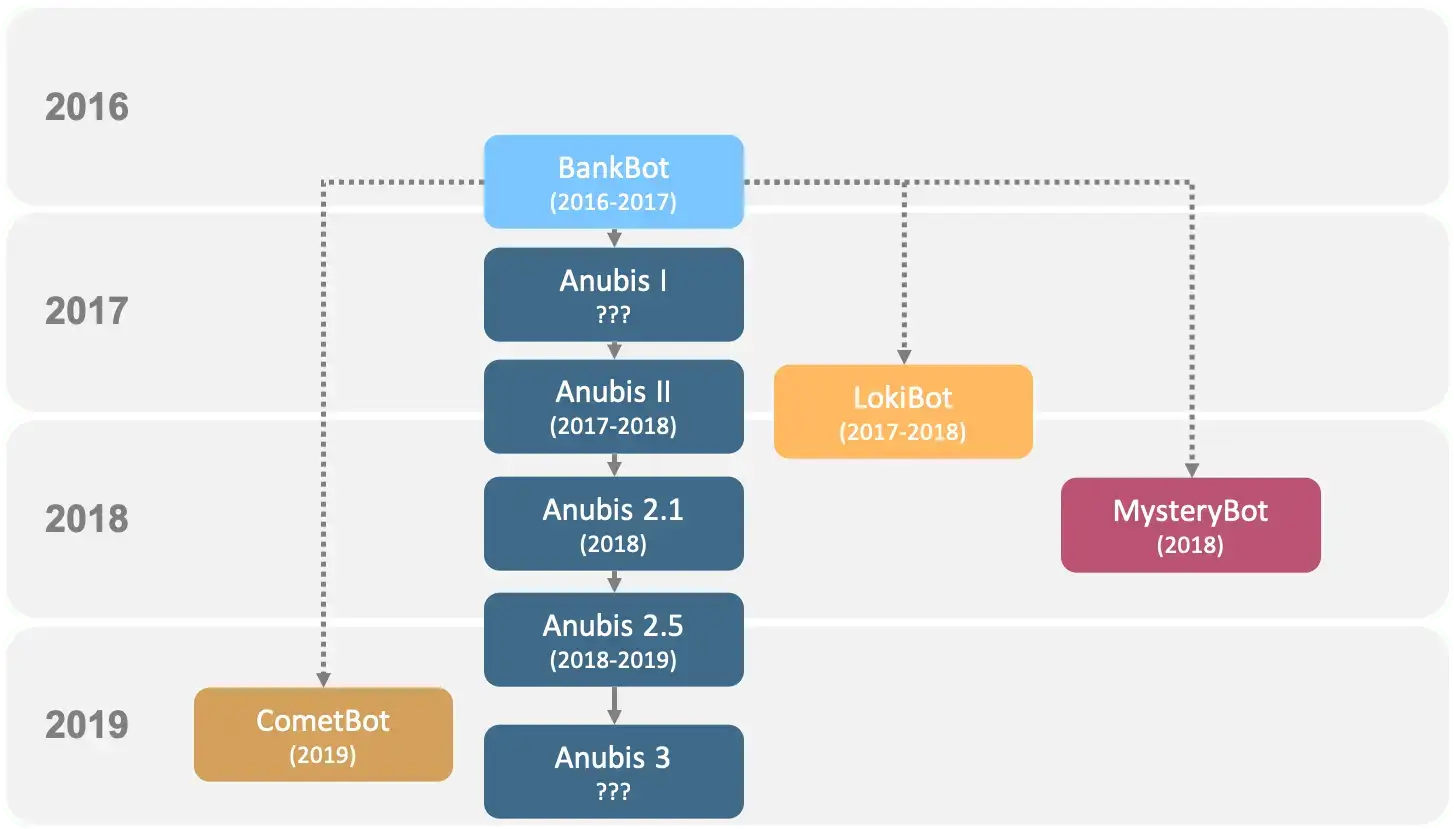
We can say that Anubis itself also sprung into existence from the publicly available BankBot code. Considering the increasing demand for Android banking malware and the fact that unobfuscated versions of the bot and the code of the admin panel of Anubis are publicly available we can definitely expect similar events.
Anubis statistics
As Anubis is a rented banking Trojan, each buyer/operator can decide the effective list of applications the Trojan should target. This results in many different campaigns with different objectives.
Although there have been several different campaigns targeting different sets of applications, when considering the average Anubis sample, the number of targets is approximately 370 unique applications.
Target locations
Based on the countries for which the targeted applications are made, it is possible to make statistics of the number of targets per region.
As can be seen in following chart, it is clear that there is a strong interest in institutions providing services in Europe, Asia and the Americas:
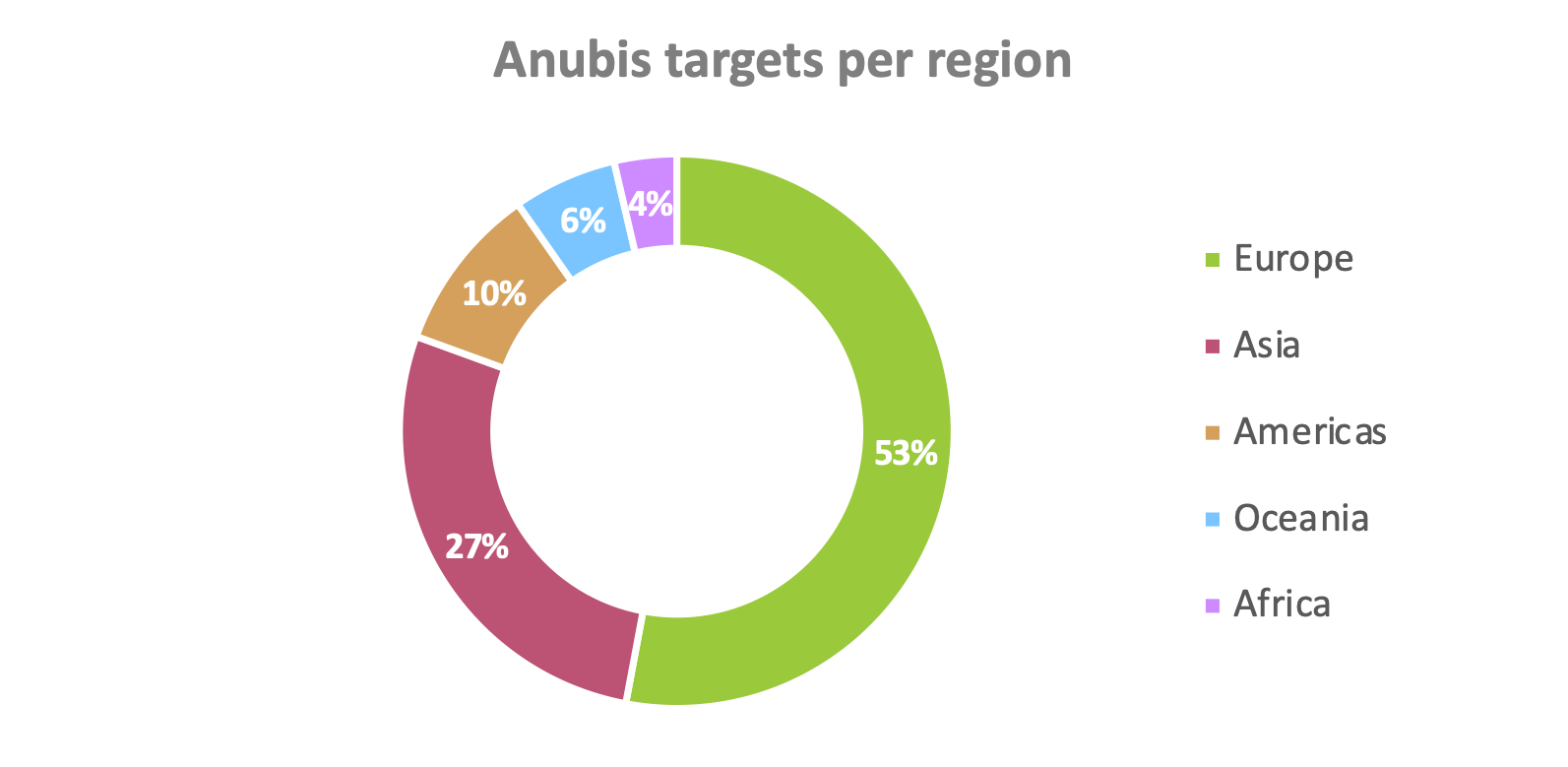
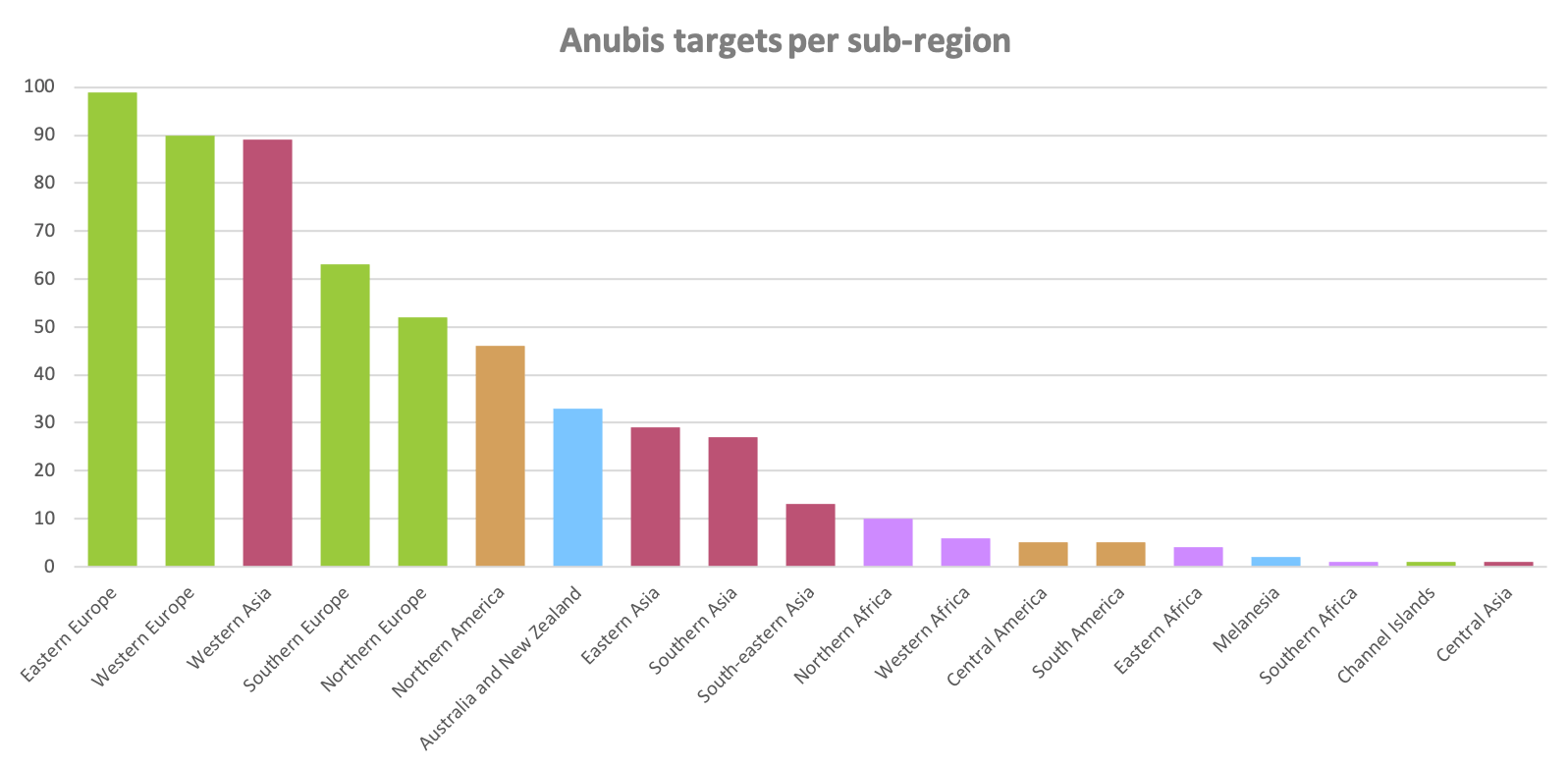
When we narrow this down to subregions we can see that the targets are in fact institutions active in Europe, West-Asia, North-America and Australia.
Interestingly, those locations match banking malware’s “usual suspects”; many of the previously observed banking malware families have been seen primarily targeting financial institutions in those subregions.
Anubis has been targeting applications from financial institutions present in more than 100 different countries. The top 20 victim countries are visible in following chart:
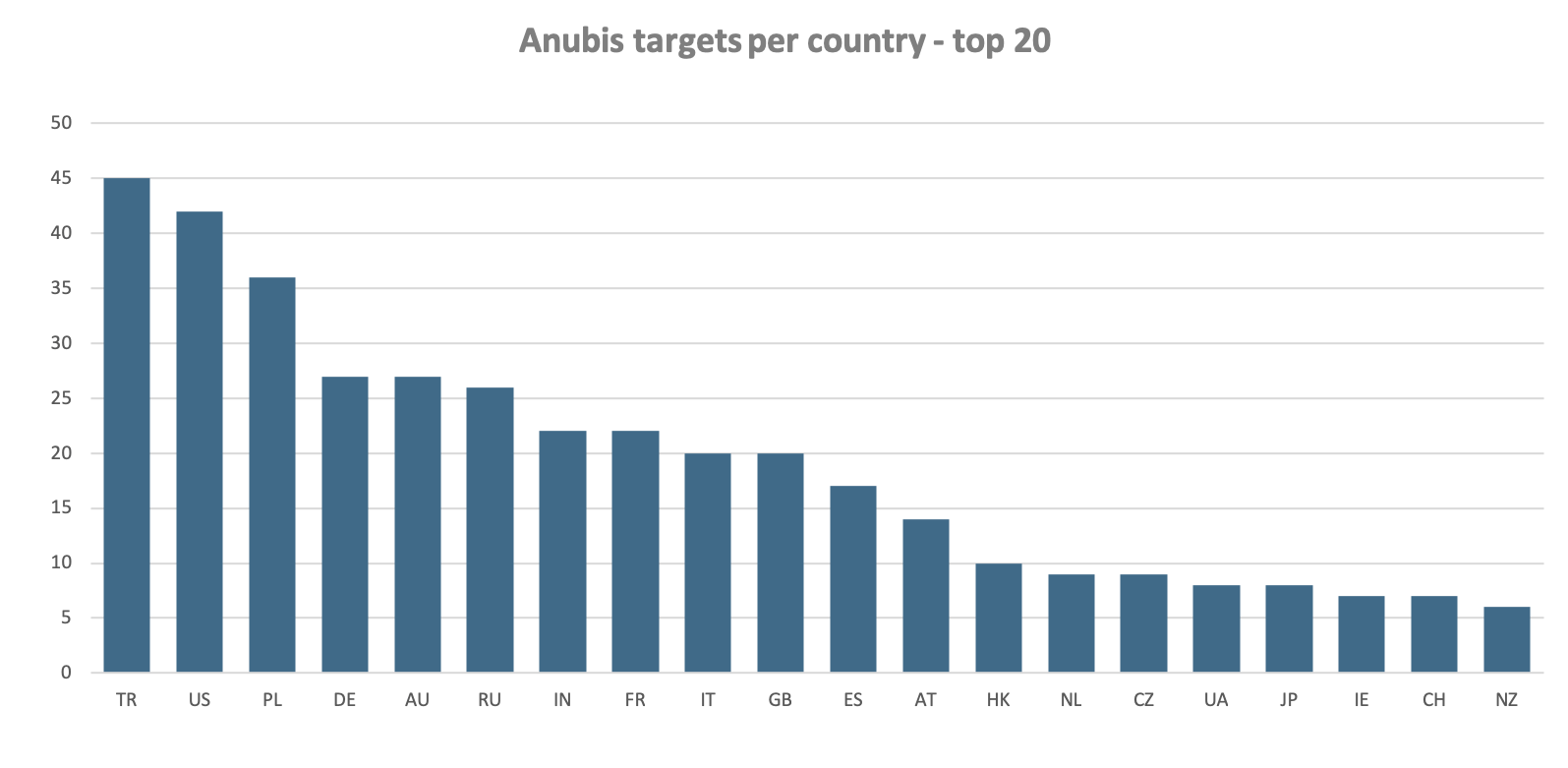
Keep in mind that statistics can be slightly biased due to certain applications serving a large number of different countries.
Target types
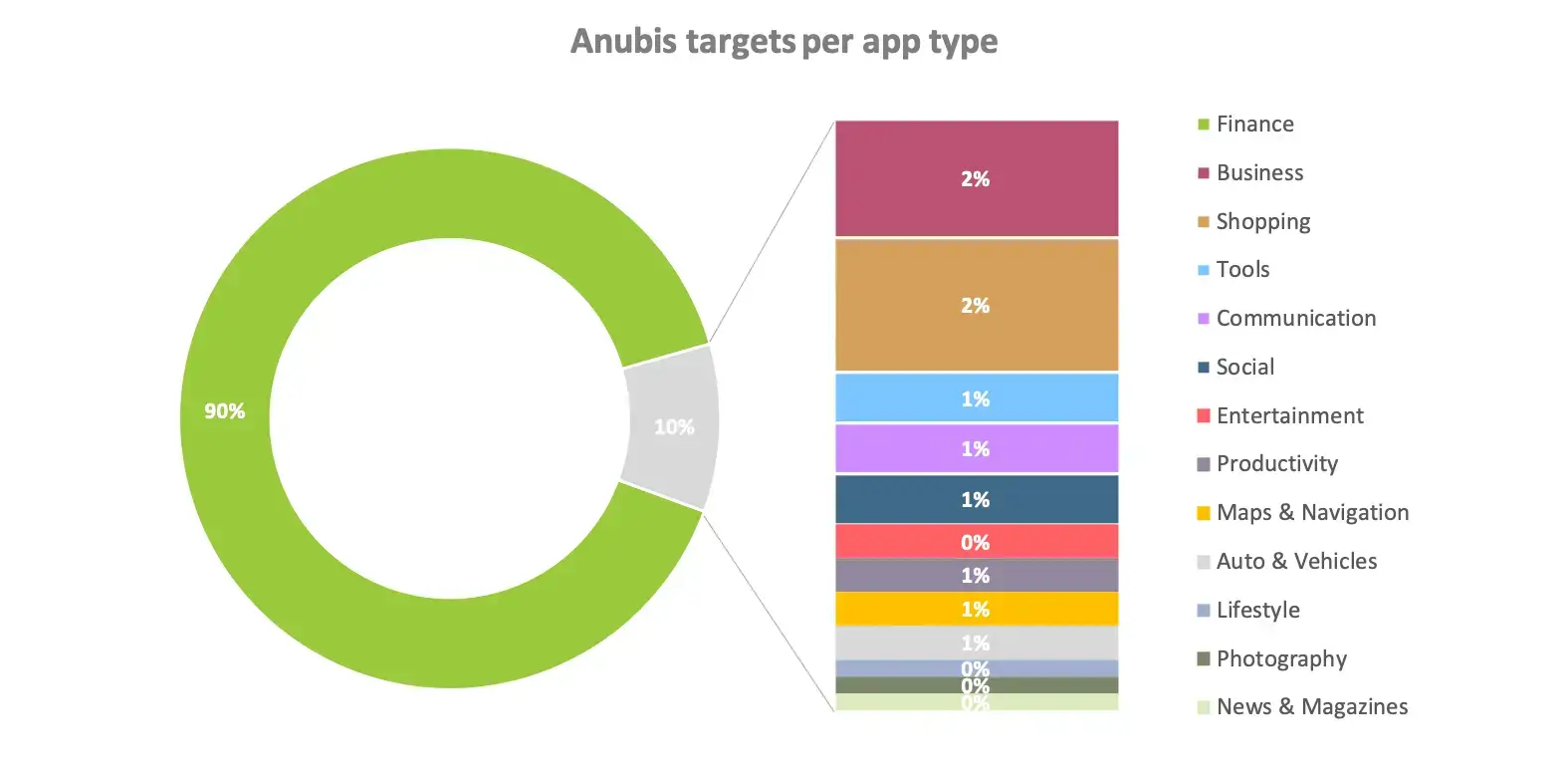
Based on the application types provided by Google, we can see based on the targeted applications that although the Anubis Trojan is a banker and therefore mainly targets “Finance” apps, it also has interest in other types of apps.
As visible in following chart, the application types in second and third position of interest are “Shopping” and “Business” apps, which can be explained by the fact that is shouldn’t look suspicious to the victim when such applications are requesting update of payment details or other sensitive information.
After “Finance” apps, the app types of second choice are “Shopping” and “Business” followed by “Tools”, “Communication” and “Social” apps. Therefore, understand that although such malware is called banking malware its aim is to perform fraud and therefore targets more than only financial apps to achieve its goal.
In conclusion, what’s next
Considering the growing demand for Android banking malware, we can definitely expect actors to continue using Anubis. Although the creator has vanished the threat is still real; the malware will continue to operate and provide its advanced features to ill-intentioned actors.
We can expect the following events to take place:
- Anubis customers having sufficient resources will continue to use the Trojan.
- As some actors have access to both the Anubis admin panel and builder it’s likely they will try to sell it by themselves.
- Some disgruntled customers having access to the sources might leak additional code and resources as retaliation.
- As it’s known that some actors have access to the right resources we can expect some enhancement and maybe even new features.
If those events indeed take place, it will result in new actors using Anubis, new campaigns and maybe even new malware variants or malware families based on the Anubis code.
Knowledge of the threat landscape and implementation of the right detection tools remains crucial to be able to protect yourself from fraud; Anubis is only one of the many Trojans active in the wild!
Mobile Threat Intelligence
Our threat intelligence solution – MTI, provides the context and in-depth knowledge of the past and present malware-powered threats in order to understand the future of the threat landscape. Such intelligence, includes both the strategic overview on trends and the operational indicators to discern early signals of upcoming threats and build a future-proof security strategy.
Client Side Detection
Our online fraud detection solution – CSD, presents financial institutions with the real-time overview on the risk status of their online channels and related devices. This overview provides all the relevant information and context to act upon threats before they turn into fraud. The connectivity with existing risk or fraud engines allows for automated and orchestrated, round the clock fraud mitigation.
Appendix
Anubis samples
Some of the latest Anubis samples found in the wild:
Build date: Mar 19 2019 App name: FlashPlayer Package name: com.qfoqzju.yrcapztuywyu
Hash: 84bb0570a862f4a74054629ae6338a4938ffc0fdad100b66fae3a279ab25df6b
Build date: Mar 18 2019 App name: Flash_Player_2019 Package name: com.ewsazh.txmypalqtgn
Hash: fdfba566e0ac5d7b0f5479068487bb4bfa2eb85d5f4eff7a8d1851b83401d850
Build date: Mar 18 2019 App name: YouTube Package name: com.dtimrfrfmlek.umvkez
Hash: b8a843bc06ee935059edf3637c717e2f2ef2f42698498df0dfe475bf944f1b08
Build date: Mar 18 2019 App name: FlashPlayer Package name: com.smijezbmbslg.dsznlnztlydj
Hash: db766146be531b813aecac731387dd38d710327b60a653a40b9fb28f22bf69eb
Build date: Mar 17 2019 App name: Sistemi Güncelle Package name: com.jqxltum.dmfkol
Hash: 2e843554c98ecfad4edef52e332a9e7e4a3d0ba40fa76c5ac9b783aca7219868
Target list
The list of mobile apps targeted by Anubis contains a total of 378 unique applications:
| Package name | Application name |
|---|---|
| MyING.be | ING Smart Banking |
| alior.bankingapp.android | Usługi Bankowe |
| at.bawag.mbanking | BAWAG P.S.K. |
| at.easybank.mbanking | easybank |
| at.easybank.securityapp | easybank Security App |
| at.easybank.tablet | easybank app |
| at.psa.app.bawag | BAWAG P.S.K. SmartPay |
| at.spardat.bcrmobile | Touch 24 Banking BCR |
| at.spardat.netbanking | ErsteBank/Sparkasse netbanking |
| at.volksbank.volksbankmobile | Volksbank Banking |
| au.com.bankwest.mobile | Bankwest |
| au.com.cua.mb | CUA |
| au.com.ingdirect.android | ING Australia Banking |
| au.com.mebank.banking | ME Bank |
| au.com.nab.mobile | NAB Mobile Banking |
| au.com.newcastlepermanent | NPBS Mobile Banking |
| au.com.suncorp.SuncorpBank | Suncorp Bank |
| biz.mobinex.android.apps.cep_sifrematik | Garanti Cep Şifrematik |
| by.st.alfa | Альфа-Бизнес Мобайл Беларусь |
| com.DijitalSahne.EnYakinHalkbank | Halkbank Nerede |
| com.FubonMobileClient | Fubon HK |
| com.MobileTreeApp | Dah Sing Bank |
| com.Plus500 | Plus500: CFD Online Trading on Forex and Stocks |
| com.SifrebazCep | Halkbank Şifrebaz Cep |
| com.abnamro.nl.mobile.payments | ABN AMRO Mobiel Bankieren |
| com.advantage.RaiffeisenBank | Raiffeisen Smart Mobile |
| com.aff.otpdirekt | OTP SmartBank |
| com.akbank.android.apps.akbank_direkt | Akbank Direkt |
| com.akbank.android.apps.akbank_direkt_tablet | Akbank Direkt Tablet |
| com.akbank.softotp | Akbank Direkt Şifreci |
| com.amazon.mShop.android.shopping | Amazon Shopping |
| com.amazon.windowshop | Amazon for Tablets |
| com.anz.android | ANZ Mobile Taiwan |
| com.anz.android.gomoney | ANZ Australia |
| com.anzspot.mobile | ANZ Spot |
| com.arubanetworks.atmanz | Atmosphere ANZ |
| com.axis.mobile | Axis Mobile- Fund Transfer,UPI,Recharge & Payment |
| com.bankaustria.android.olb | Bank Austria MobileBanking |
| com.bankia.wallet | Bankia Wallet |
| com.bankinter.launcher | Bankinter Móvil |
| com.bankofamerica.cashpromobile | CashPro® + Token |
| com.bankofqueensland.boq | BOQ Mobile |
| com.barclays.android.barclaysmobilebanking | Barclays Mobile Banking |
| com.barclays.ke.mobile.android.ui | Barclays Kenya |
| com.bawagpsk.securityapp | BAWAG P.S.K. Security App |
| com.bbva.bbvacontigo | BBVA Spain |
| com.bbva.bbvawallet | BBVA Wallet Spain. Mobile Payment |
| com.bbva.netcash | BBVA Net cash | ES & PT |
| com.bendigobank.mobile | Bendigo Bank |
| com.binance.dev | Binance - Cryptocurrency Exchange |
| com.binance.odapplications | Binance: Cryptocurrency & Bitcoin Exchange |
| com.bitcoin.ss.zebpayindia | Zebpay India |
| com.bitfinex.bfxapp | Bitfinex |
| com.bitmarket.trader | Aplikacja Bitmarket |
| com.blockfolio.blockfolio | Blockfolio - Bitcoin and Cryptocurrency Tracker |
| com.bmo.mobile | BMO Mobile Banking |
| com.boursorama.android.clients | Boursorama Banque |
| com.bssys.VTBClient | Mobile Client VTB |
| com.bssys.vtb.mobileclient | MobileClientVTB |
| com.btcturk | BtcTurk Bitcoin Borsası |
| com.caisseepargne.android.mobilebanking | Banque |
| com.cba.android.netbank | CommBank app for tablet |
| com.chase.sig.android | Chase Mobile |
| com.cibc.android.mobi | CIBC Mobile Banking® |
| com.citi.citimobile | Citi Mobile® |
| com.citibank.mobile.au | Citibank Australia |
| com.citibank.mobile.uk | Citi Mobile UK |
| com.clairmail.fth | Fifth Third Mobile Banking |
| com.cleverlance.csas.servis24 | SERVIS 24 Mobilni banka |
| com.cm_prod.bad | Crédit Mutuel |
| com.cm_prod.epasal | Epargne Salariale CM |
| com.cm_prod.nosactus | Crédit Mutuel - Nos Actus |
| com.cm_prod_tablet.bad | Crédit Mutuel pour Tablettes |
| com.coin.profit | Coin Profit |
| com.coinbase.android | Coinbase - Buy Bitcoin & more. Secure Wallet. |
| com.coins.bit.local | LocalBitCoins |
| com.coins.ful.bit | LocalBitCoins NEW |
| com.comarch.mobile.banking.bgzbnpparibas.biznes | Mobile BiznesPl@net |
| com.comarch.security.mobilebanking | INGBusiness |
| com.commbank.netbank | CommBank |
| com.crowdcompass.appSQ0QACAcYJ | ANZ Investor Tour |
| com.crypter.cryptocyrrency | Crypto App - Widgets, Alerts, News, Bitcoin Prices |
| com.csam.icici.bank.imobile | iMobile by ICICI Bank |
| com.db.mm.deutschebank | Meine Bank |
| com.db.mm.norisbank | norisbank App |
| com.db.pwcc.dbmobile | Deutsche Bank Mobile |
| com.dbs.hk.dbsmbanking | DBS digibank Hong Kong |
| com.de.dkb.portalapp | DKB-Banking |
| com.ebay.mobile | Fashion & Tech Deals - Shop, Sell & Save with eBay |
| com.edsoftapps.mycoinsvalue | My CryptoCoins Portfolio - All Coins |
| com.empik.empikapp | Empik |
| com.empik.empikfoto | Empik Foto |
| com.entersekt.authapp.sparkasse | S-ID-Check |
| com.fi6122.godough | TSB Mobile |
| com.finansbank.mobile.cepsube | QNB Finansbank Cep Şubesi |
| com.finanteq.finance.ca | CA24 Mobile |
| com.fragment.akbank | Akbank Sanat |
| com.fusion.ATMLocator | People’s Choice Credit Union |
| com.garanti.cepbank | Garanti CepBank |
| com.garanti.cepsubesi | Garanti Mobile Banking |
| com.garantibank.cepsubesiro | GarantiBank |
| com.garantiyatirim.fx | Garanti FX Trader |
| com.getingroup.mobilebanking | Getin Mobile |
| com.grppl.android.shell.BOS | Bank of Scotland Mobile Banking: secure on the go |
| com.grppl.android.shell.CMBlloydsTSB73 | Lloyds Bank Mobile Banking |
| com.grppl.android.shell.halifax | Halifax: the banking app that gives you extra |
| com.hangseng.rbmobile | Hang Seng Personal Banking |
| com.htsu.hsbcpersonalbanking | HSBC Mobile Banking |
| com.idamob.tinkoff.android | Tinkoff |
| com.idbi.mpassbook | IDBI Bank mPassbook |
| com.idbibank.abhay_card | Abhay by IDBI Bank Ltd |
| com.ideomobile.hapoalim | בנק הפועלים - ניהול החשבון |
| com.ifs.banking.fiid4202 | TSBBank Mobile Banking |
| com.imb.banking2 | IMB.Banking |
| com.infonow.bofa | Bank of America Mobile Banking |
| com.infrasofttech.indianBank | IndPay |
| com.ing.diba.mbbr2 | ING-DiBa Banking + Brokerage |
| com.ing.mobile | ING Bankieren |
| com.ingbanktr.ingmobil | ING Mobil |
| com.isis_papyrus.raiffeisen_pay_eyewdg | Raiffeisen ELBA |
| com.jackpf.blockchainsearch | Bitcoin Blockchain Explorer |
| com.jamalabbasii1998.localbitcoin | Local BitCoin |
| com.jiffyondemand.user | Jiffy |
| com.konylabs.capitalone | Capital One® Mobile |
| com.kryptokit.jaxx | Jaxx Blockchain Wallet |
| com.kutxabank.android | Kutxabank |
| com.kuveytturk.mobil | Mobil Şube |
| com.latuabanca_tabperandroid | La tua banca per Tablet |
| com.latuabancaperandroid | Intesa Sanpaolo Mobile |
| com.localbitcoins.exchange | LocalBitcoins - Buy and sell Bitcoin |
| com.localbitcoinsmbapp | LocalBitCoins Official |
| com.lynxspa.bancopopolare | YouApp |
| com.magiclick.FinansPOS | FinansPOS |
| com.magiclick.odeabank | Odeabank |
| com.mal.saul.coinmarketcap | Coin Market-Bitcoin Prices,Currencies,BTC,EUR,ICO |
| com.matriksdata.finansyatirim | QNB Finansinvest |
| com.matriksdata.ziraatyatirim.pad | Ziraat Trader HD |
| com.matriksmobile.android.ziraatTrader | Ziraat Trader |
| com.mobikwik_new | Mobile Recharge,Bill Payments,UPI & Money Transfer |
| com.mobillium.papara | Papara Cüzdan |
| com.moneybookers.skrillpayments | Skrill |
| com.moneybookers.skrillpayments.neteller | NETELLER |
| com.monitise.isbankmoscow | ISBANK Online |
| com.mtel.androidbea | BEA 東亞銀行 |
| com.mycelium.wallet | Mycelium Bitcoin Wallet |
| com.oxigen.oxigenwallet | Bill Payment & Recharge,Wallet |
| com.palatine.android.mobilebanking.prod | ePalatine Particuliers |
| com.paypal.android.p2pmobile | PayPal Cash App: Send and Request Money Fast |
| com.phyder.engage | RBS |
| com.plunien.poloniex | Poloniex |
| com.portfolio.coinbase_tracker | Coinbase Tracker (3rd party) |
| com.pozitron.albarakaturk | Albaraka Mobil Şube |
| com.pozitron.iscep | İşCep |
| com.pozitron.vakifbank | VakıfBank Cep Şifre |
| com.quickmobile.anzirevents15 | ANZ Investor Relations Events |
| com.rbc.mobile.android | RBC Mobile |
| com.rbs.mobile.android.natwest | NatWest Mobile Banking |
| com.rbs.mobile.android.natwestbandc | NatWest Business Banking |
| com.rbs.mobile.android.natwestoffshore | NatWest International |
| com.rbs.mobile.android.rbs | Royal Bank of Scotland Mobile Banking |
| com.rbs.mobile.android.rbsbandc | RBS Business Banking |
| com.rbs.mobile.android.ubr | Ulster Bank RI Mobile Banking |
| com.rbs.mobile.investisir | RBS Investor & Media Relations |
| com.redrockdigimark | QNB National Day |
| com.rsi | ruralvía |
| com.santander.app | Santander Brasil |
| com.sbi.SBIFreedomPlus | SBI Anywhere Personal |
| com.scb.breezebanking.hk | SC Mobile Hong Kong |
| com.scotiabank.mobile | Scotiabank Mobile Banking |
| com.snapwork.IDBI | IDBI Bank GO Mobile+ |
| com.snapwork.hdfc | HDFC Bank MobileBanking |
| com.softtech.isbankasi | İşTablet |
| com.softtech.iscek | ÇEKSOR |
| com.sovereign.santander | Santander Bank US |
| com.starfinanz.mobile.android.pushtan | S-pushTAN |
| com.starfinanz.smob.android.sbanking | Sparkasse+ Finanzen im Griff |
| com.starfinanz.smob.android.sfinanzstatus | Sparkasse Ihre mobile Filiale |
| com.starfinanz.smob.android.sfinanzstatus.tablet | Sparkasse fürs Tablet |
| com.suntrust.mobilebanking | SunTrust Mobile App |
| com.targo_prod.bad | TARGOBANK Mobile Banking |
| com.td | TD Canada |
| com.teb | CEPTETEB |
| com.tecnocom.cajalaboral | Banca Móvil Laboral Kutxa |
| com.thunkable.android.manirana54.LocalBitCoins | LocalBitCoins |
| com.thunkable.android.manirana54.LocalBitCoins_unblock | UNBLOCK Local BitCoins |
| com.thunkable.android.santoshmehta364.UNOCOIN_LIVE | UNOCOIN LIVE |
| com.tmob.denizbank | MobilDeniz |
| com.tmob.tabletdeniz | MobilDeniz Tablet |
| com.tmobtech.halkbank | Halkbank Mobil |
| com.tnx.apps.coinportfolio | Coin Portfolio for Bitcoin & Altcoin tracker |
| com.triodos.bankingnl | Triodos Bankieren NL |
| com.unicredit | Mobile Banking UniCredit |
| com.unionbank.ecommerce.mobile.android | Union Bank Mobile Banking |
| com.unionbank.ecommerce.mobile.commercial.legacy | Union Bank Commercial Clients |
| com.unocoin.unocoinmerchantPoS | Unocoin Merchant PoS |
| com.unocoin.unocoinwallet | Unocoin Wallet |
| com.usaa.mobile.android.usaa | USAA Mobile |
| com.usbank.mobilebanking | U.S. Bank |
| com.vakifbank.mobile | VakıfBank Mobil Bankacılık |
| com.veripark.ykbaz | YapıKredi Azərbaycan MobilBank |
| com.vipera.ts.starter.QNB | QNB Mobile |
| com.vtb.mobilebank | VTB Mobile Georgia |
| com.wellsFargo.ceomobile | Wells Fargo CEO Mobile® |
| com.wf.wellsfargomobile | Wells Fargo Mobile |
| com.wf.wellsfargomobile.tablet | Wells Fargo for Tablet |
| com.yinzcam.facilities.verizon | Capital One Arena Mobile |
| com.ykb.android | Yapı Kredi Mobile |
| com.ykb.android.mobilonay | Yapı Kredi Corporate-For Firms |
| com.ykb.androidtablet | Yapı Kredi Mobil Şube |
| com.ykb.avm | Yapı Kredi Cüzdan |
| com.yurtdisi.iscep | JSC İŞBANK |
| com.ziraat.ziraatmobil | Ziraat Mobil |
| com.ziraat.ziraattablet | Ziraat Tablet |
| cz.airbank.android | My Air |
| cz.csob.smartbanking | ČSOB SmartBanking |
| cz.sberbankcz | Smart Banking |
| de.comdirect.android | comdirect mobile App |
| de.commerzbanking.mobil | Commerzbank Banking App |
| de.consorsbank | Consorsbank |
| de.dkb.portalapp | DKB-Banking |
| de.fiducia.smartphone.android.banking.vr | VR-Banking |
| de.fiducia.smartphone.android.securego.vr | VR-SecureGo |
| de.postbank.finanzassistent | Postbank Finanzassistent |
| de.schildbach.wallet | Bitcoin Wallet |
| es.bancopopular.nbmpopular | Popular |
| es.bancosantander.apps | Santander |
| es.cm.android | Bankia |
| es.cm.android.tablet | Bankia Tablet |
| es.evobanco.bancamovil | EVO Banco móvil |
| es.lacaixa.mobile.android.newwapicon | CaixaBank |
| eu.eleader.mobilebanking.invest | plusbank24 |
| eu.eleader.mobilebanking.pekao | Pekao24Makler |
| eu.eleader.mobilebanking.pekao.firm | PekaoBiznes24 |
| eu.eleader.mobilebanking.raiffeisen | Mobile Bank |
| eu.inmite.prj.kb.mobilbank | Mobilni Banka |
| eu.newfrontier.iBanking.mobile.Halk.Retail | Halkbank Mobile App |
| eu.unicreditgroup.hvbapptan | HVB Mobile B@nking |
| finansbank.enpara | Enpara.com Cep Şubesi |
| finansbank.enpara.sirketim | Enpara.com Şirketim Cep Şubesi |
| fr.axa.monaxa | Mon AXA |
| fr.banquepopulaire.cyberplus | Banque Populaire |
| fr.creditagricole.androidapp | Ma Banque |
| fr.laposte.lapostemobile | La Poste - Services Postaux |
| fr.laposte.lapostetablet | La Poste HD - Services Postaux |
| fr.lcl.android.customerarea | Mes Comptes - LCL |
| hdfcbank.hdfcquickbank | HDFC Bank MobileBanking LITE |
| hk.com.hsbc.hsbchkmobilebanking | HSBC HK Mobile Banking |
| hr.asseco.android.jimba.mUCI.ro | Mobile Banking |
| in.co.bankofbaroda.mpassbook | Baroda mPassbook |
| info.blockchain.merchant | Blockchain Merchant |
| io.getdelta.android | Delta - Bitcoin & Cryptocurrency Portfolio Tracker |
| it.bnl.apps.banking | BNL |
| it.bnl.apps.enterprise.bnlpay | BNL PAY |
| it.bpc.proconl.mbplus | MB+ |
| it.copergmps.rt.pf.android.sp.bmps | Banca MPS |
| it.gruppocariparma.nowbanking | Nowbanking |
| it.ingdirect.app | ING DIRECT Italia |
| it.nogood.container | UBI Banca |
| it.popso.SCRIGNOapp | SCRIGNOapp |
| it.secservizi.mobile.atime.bpaa | Volksbank per tablet |
| it.volksbank.android | Volksbank · Banca Popolare |
| jp.co.aeonbank.android.passbook | イオン銀行通帳アプリ かんたんログイン&残高・明細の確認 |
| jp.co.netbk | 住信SBIネット銀行 |
| jp.co.rakuten_bank.rakutenbank | 楽天銀行 -個人のお客様向けアプリ |
| jp.co.sevenbank.AppPassbook | App Bankbook |
| jp.co.smbc.direct | 三井住友銀行アプリ |
| jp.mufg.bk.applisp.app | 三菱UFJ銀行 |
| me.doubledutch.hvdnz.cbnationalconference2016 | CB Conference 2018 |
| mobi.societegenerale.mobile.lappli | L’Appli Société Générale |
| mobile.santander.de | Santander Mobile Banking |
| net.bnpparibas.mescomptes | Mes Comptes BNP Paribas |
| nl.asnbank.asnbankieren | ASN Mobiel Bankieren |
| nl.snsbank.mobielbetalen | SNS Mobiel Betalen |
| nz.co.anz.android.mobilebanking | ANZ goMoney New Zealand |
| nz.co.asb.asbmobile | ASB Mobile Banking |
| nz.co.bnz.droidbanking | BNZ Mobile |
| nz.co.kiwibank.mobile | Kiwibank Mobile Banking |
| nz.co.westpac | Westpac One (NZ) Mobile Banking |
| org.banksa.bank | BankSA Mobile Banking |
| org.bom.bank | Bank of Melbourne Mobile Banking |
| org.stgeorge.bank | St.George Mobile Banking |
| org.westpac.bank | Westpac Mobile Banking |
| piuk.blockchain.android | Blockchain Wallet. Bitcoin, Bitcoin Cash, Ethereum |
| pl.aliorbank.aib | Alior Bank |
| pl.allegro | Allegro |
| pl.bosbank.mobile | BOŚBank24 |
| pl.bph | BusinessPro Lite |
| pl.bps.bankowoscmobilna | BPS Mobilnie |
| pl.bzwbk.bzwbk24 | Santander mobile |
| pl.bzwbk.ibiznes24 | iBiznes24 mobile |
| pl.bzwbk.mobile.tab.bzwbk24 | BZWBK24 mobile (tablet) |
| pl.ceneo | Ceneo - zakupy i promocje |
| pl.com.rossmann.centauros | Rossmann PL |
| pl.fmbank.smart | Nest Bank |
| pl.ideabank.mobilebanking | Idea Bank PL |
| pl.ing.mojeing | Moje ING mobile |
| pl.ipko.mobile | Token iPKO |
| pl.mbank | mBank PL |
| pl.millennium.corpApp | Bank Millennium for Companies |
| pl.orange.mojeorange | Mój Orange |
| pl.pkobp.iko | IKO |
| pl.pkobp.ipkobiznes | iPKO biznes |
| posteitaliane.posteapp.apppostepay | Postepay |
| ro.btrl.mobile | Banca Transilvania |
| ru.alfabank.mobile.android | Альфа-Банк (Alfa-Bank) |
| ru.alfabank.oavdo.amc | Альфа-Бизнес |
| ru.alfabank.sense | Sense от Альфа-Банка |
| ru.alfadirect.app | Alfa-Direct |
| ru.bm.mbm | ВТБ Банк Москвы |
| ru.mw | QIWI Wallet |
| ru.sberbank.mobileoffice | Сбербанк Бизнес Онлайн |
| ru.sberbank.sberbankir | Sberbank IR |
| ru.sberbank.spasibo | Спасибо от Сбербанка |
| ru.sberbank_sbbol | Сбербанк Бизнес Онлайн |
| ru.sberbankmobile | Сбербанк Онлайн |
| ru.tcsbank.c2c | Card 2 Card |
| ru.tinkoff.goabroad | FSSP FNS Russia |
| ru.tinkoff.mgp | Tinkoff Play: apply for a card |
| ru.tinkoff.sme | Тинькофф Бизнес |
| ru.vtb24.mobilebanking.android | VTB-Online |
| sk.sporoapps.accounts | Účty |
| sk.sporoapps.skener | Platby |
| src.com.idbi | IDBI Bank GO Mobile |
| tr.com.hsbc.hsbcturkey | HSBC Turkey |
| tr.com.sekerbilisim.mbank | ŞEKER MOBİL ŞUBE |
| tr.com.tradesoft.tradingsystem.gtpmobile.halk | Halk Trade |
| uk.co.bankofscotland.businessbank | Bank of Scotland Business Mobile Banking |
| uk.co.santander.businessUK.bb | Business Banking |
| uk.co.santander.santanderUK | Santander Mobile Banking |
| wit.android.bcpBankingApp.millenniumPL | Bank Millennium |
| wos.com.zebpay | Zebpay Calculator - Profit/Loss Management |
| zebpay.Application | Zebpay Bitcoin and Cryptocurrency Exchange |
| aib.ibank.android | AIB Mobile |
| com.att.myWireless | myAT&T |
| com.bbnt | BB&T PlanTrac Mobile |
| com.bestbuy.android | Best Buy |
| com.discoverfinancial.mobile | Discover Mobile |
| com.eastwest.mobile | EastWest Mobile |
| com.fi6256.godough | Commercial Bank for Android |
| com.fi6543.godough | Community Bank NA Mobile |
| com.fi6665.godough | Fifth District Mobile Banking |
| com.fi9228.godough | CNB Mobile Banking |
| com.fi9908.godough | First US Bank Anywhere Access |
| com.fuib.android.spot.online | PUMB Online |
| com.idamobile.android.hcb | Мобильный банк - Хоум Кредит |
| com.ifs.banking.fiid1369 | Fulton Bank Mobile Banking |
| com.ifs.mobilebanking.fiid3919 | Associated Credit Union Mobile |
| com.jackhenry.rockvillebankct | United Bank - Mobile Banking |
| com.jackhenry.washingtontrustbankwa | WTB Mobile |
| com.jpm.sig.android | J.P. Morgan Mobile |
| com.sterling.onepay | Sterling OnePay |
| com.svb.mobilebanking | SVB Mobile Banking-Commercial |
| com.ukrsibbank.client.android | UKRSIB online |
| com.vkontakte.android | VK |
| com.vzw.hss.myverizon | My Verizon |
| logo.com.mbanking | ПСБ |
| org.usemployees.mobile | U.S. Employees Credit Union |
| pinacleMobileiPhoneApp.android | PINACLE® |
| ru.alfabank.mobile.ua.android | Alfa-Mobile Ukraine |
| ru.avangard | Банк Авангард |
| ru.rosbank.android | ROSBANK Online |
| ru.simpls.brs2.mobbank | Моб. банк Русский Стандарт |
| ru.simpls.mbrd.ui | МТС Банк |
| ru.taxovichkof.android | TaxovichkoF: order a taxi in St Petersburg online |
| ua.aval.dbo.client.android | Raiffeisen Online Ukraine |
| ua.com.cs.ifobs.mobile.android.otp | OTP Smart |
| ua.com.cs.ifobs.mobile.android.pivd | Pivdenny MyBank |
| ua.oschadbank.online | Ощад 24/7 |
| ua.privatbank.ap24 | Privat24 |
| xmr.org.freewallet.app | Monero Wallet |
| com.ubercab | Uber |
| com.avito.android | Объявления Авито: авто, работа, квартиры, вещи |
| com.instagram.android | |
| com.openbank | Банк Открытие |
| com.twitter.android | |
| com.viber.voip | Viber Messenger |
| com.whatsapp | WhatsApp Messenger |
| org.telegram.messenger | Telegram |
| ru.auto.ara | Авто.ру: купить и продать авто |
| ru.ok.android | OK |
| ru.rutaxi.vezet | Везёт – заказ такси онлайн |
| ru.yandex.taxi | Yandex.Taxi Ride-Hailing Service |
| cb.ibank | УБРиР |
| com.bifit.mobile.otpbank | ОТПбизнес |
| com.bifit.mobile.ubrr | УБРиР Pro |
| com.bifit.mobile.zenit | ЗЕНИТ Бизнес |
| com.bssys.mbcphone.akbars | АК БАРС Мобильный для Бизнеса |
| com.bssys.mbcphone.mts | MTS Bank. Business Client |
| com.bssys.mbcphone.rsbank | РС Бизнес Онлайн |
| com.bssys.mbcphone.ubrir | УБРиР Light |
| com.bssys.mbcphone.vostochny | Восточный Корпоративный |
| com.citibank.mobile.ru | Citibank RU |
| com.isimplelab.ibank.kazan | Банк Казани |
| com.isimplelab.isimpleceo.kazan | БК Бизнес |
| com.isimplelab.isimpleceo.minb | МИнБанк Бизнес |
| cz.bsc.rc | Ренессанс Кредит |
| ru.akbars.mobile | Ак Барс Онлайн 3.0 |
| ru.avangard.legal | Авангард Бизнес |
| ru.bankuralsib.mb.android | Мобильный банк УРАЛСИБ |
| ru.beeline.card | Карта Билайн |
| ru.bspb | BSPB Mobile |
| ru.ftc.faktura.expressbank | Восточный мобайл |
| ru.gazprombank.android.mobilebank.app | Телекард 2.0 |
| ru.kykyryza | Кукуруза |
| ru.mdm.app | Бинбанк Бизнес |
| ru.minbank.android | МИнБ |
| ru.mkb.business | МКБ Бизнес |
| ru.mkb.mobile | МКБ Мобайл |
| ru.otpbank | ОТПкредит |
| ru.psbank.msb.dev.psb_appstore | PSB Мой Бизнес |
| ru.raiffeisen.android.rbo | Райффайзен Бизнес |
| ru.raiffeisennews | Raiffeisen Online Russia |
| ru.rocketbank.r2d2 | Рокетбанк |
| ru.rshb.dbo | Мобильный банк, Россельхозбанк |
| ru.rshb.dboul | Россельхозбанк Бизнес-Онлайн |
| ru.skbbank.ib | СКБ Онлайн |
| ru.skbbank.ibank | СКБ-банк |
| ru.stepup.MDMmobileBank | Бинбанк online 2.0 |
| ru.ucb.android | Mobile.UniCredit |
| ru.vtb24.biz.client.android | ВТБ Бизнес Онлайн |
| ru.zenit.android | ЗЕНИТ Онлайн 2.0 |
| de.ingdiba.bankingapp | ING-DiBa Banking to go |
| btc.org.freewallet.app | Bitcoin Wallet by Freewallet |
| com.alibaba.aliexpresshd | AliExpress - Smarter Shopping, Better Living |
| com.bitcoin.mwallet | Bitcoin Wallet |
| com.bitpay.wallet | BitPay – Secure Bitcoin Wallet |
| com.blocktrail.mywallet | BTC.com - Bitcoin Wallet |
| com.booking | Booking.com Travel Deals |
| com.electroneum.mobile | Electroneum |
| com.gettaxi.android | Gett |
| com.google.android.play.games | Google Play Games |
| com.samsung.android.spay | Samsung Pay |
| io.totalcoin.wallet | Bitcoin Wallet Totalcoin - Buy and Sell Bitcoin |
| ru.aviasales | Aviasales — авиабилеты дешево |
| ru.tutu.tutu_emp | Tutu.ru - flights, Russian railway and bus tickets |
| ru.yandex.money | Yandex.Money—wallet, cards, transfers, and fines |
| com.google.android.apps.walletnfcrel | Google Pay |