Exobot Android Malware spreading via Google Play Store
01 January 2018
Jump to
Context
Exobot Actor (nicknamed “android”) started a new Android bot rental service named Exobot v1 in June 2016. The malware in use was built to be able to target many banks with so called overlay attacks (also known as injects). ThreatFabric’s team analyzed and researched Exobot v1, which is covered in detail in our blog.
After a year of successful campaign of Exobot v1, in May 2017 the actor “android” decided to create a new version of the malware almost from scratch, dubbed Exobot v2. At some point the actor even boldly sold Exobot via a public website (“exoandroidbot.net” was online for more than half a year), which is very uncommon for banking Trojans.
The new bot capabilities of Exobot v2 where covered in another Threatfabric blog. What made version 2 special was the bot features. Those features are by far better and comprehensive than any other Android banking Trojans such as Mazar 3.0, Lokibot v2 or Anubis 2 (alias Bankbot v2), which resulted in their success. The actor did not only focus on obfuscation of the bot code to lower its detection rate (FUD), but also on features that could bypass fraud detection mechanisms, such as the use of a SOCKS5 proxy on victim device to actually perform the transaction from the victim’s device (we have even seen requests from underground buyers for an embedded VNC module). Going this direction is giving android bankers Trojans RAT-capabilities, which we forecasted earlier in 2017. We expect that Android bankers will continue to develop stable RAT-capabilities the coming year since the source of the strongest Android banker is now in the hands of many new actors!
The recent changes
Early December 2017 the actor behind Exobot, nicknamed “android”, advertised in an underground forum that he would sell the source code of his malware to a limited number of buyers before quitting the business.
According to this same statement, he became very rich. Such a statement in the malware world generally means one of the following two things: Either the actor notices the surge of interest from law enforcement and/or competitors fighting back their market share, either his business has indeed been very fruitful and is ratio risk/gain is no longer of interest.
Taking a glance at the research we have made into the Exobot malware since its first campaign, early 2016 (when the malware was still known under the name of Marcher), we believe his statement is truth as it has been a widely spread and fully functional malware.
Sales of a Trojan’s source code usually results in the arrival on the market of new malware versions with additional capabilities and new threat actors experimenting with different means of malware distribution (snowball effect). This was seen with the malwares Slempo (sold in 2015 and leaked in 2016) and Bankbot v1 (leaked during 2016).
Less than a month after the actor started selling the Exobot source code, new campaigns in Austria, England, Netherlands and Turkey where discovered. During our investigation, we were surprised to discover that the bot count (number of infected devices) in Turkey was three times higher than those of botnets targeting other countries.
We made the link between most of the new Exobot botnets and Smishing (SMS phishing) or hybrid (desktop/mobile) phishing campaigns, but had to get hands on specific malicious apps used to infect Turkish Android users, to explain the high number of victims.
New Exobot campaign
New apps dropping Exobot malware via Google Play
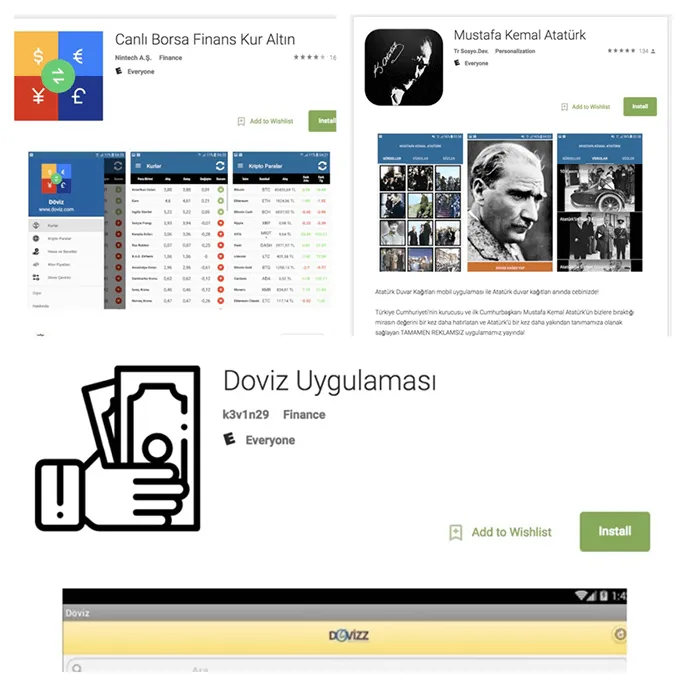
On 14 December 2017, ThreatFabric researchers discovered a new malware distribution campaign targeting Turkish users via dropper apps present in the Google Play Store. These droppers installed on thousands of phones were spreading Exobot for two new botnets operated by Turkish actors.
The use of this new means of distribution explains the significantly higher bot count in Turkey. The campaign is ongoing at the time of writing and the Turkish actors seem to have a lot of success performing financial fraud on the targeted Turkish banks (please refer to IOC section below).
Poorly hidden droppers for poorly protected store
ThreatFabric researchers have often experienced actors using droppers as spreading Modus Operandi, for example with previous campaigns for malwares such as Bankbot or Red Alert in Q1 and Q4 of 2017 and even with private Android Trojans. What really stands out in this particular campaign is that the dropper app does not even use code obfuscation or long sleep periods (which are common anti-detection technics) in attempt to bypass the Google Play Store security measures.
This raises the question of how it is possible that these apps managed to bypass the Google Play Store malware protection controls. Based on our experience we can confirm that even the simplest behavior based detection should have caught these malicious apps.
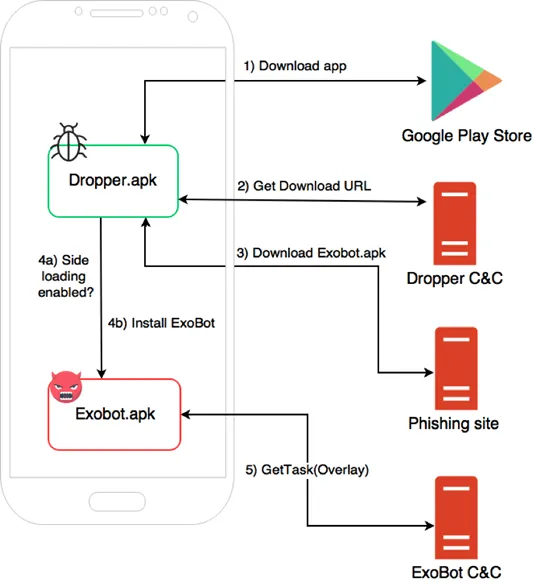
Step by step dropper MO
The dropper app works as following:
1) The victim installs the dropper from the Google Play Store, it is usually hidden in a third-party app such as social media, games or utilities (not abusing the bank identity to avoid being detected).
2) Once on the device, the dropper requests a link to the Exobot malware installer, from the dropper C&C server.
3) The dropper proceeds to download the Exobot installer.
4) As the malware itself isn’t hosted on the Google Play store it won’t be recognized as an app from a trustable source, therefore only if setting unknown sources (allowing installation from other sources than Google Play) is enabled, the Exobot malware is installed on victim’s device.
The picture below describes the different steps of the infection:
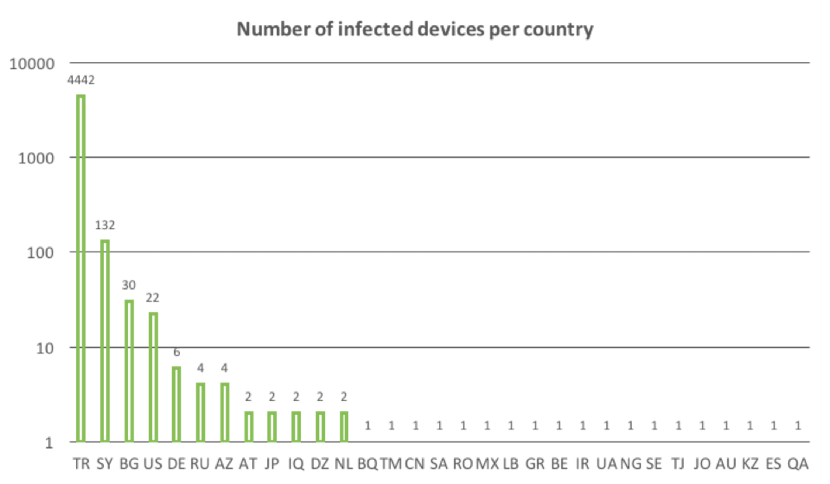
The “usveryfood” botnet
An interest in the Turkish market
This dropper campaign is linked to two Exobot botnets, both particularly focused on Turkey, due to the fact that the actors behind those specific botnets are also Turkish.
The chart below represents statistics of one of these botnets, called “usveryfood”. As you can see, the bots are mainly concentrated in Turkey (logarithmic scale). This is followed by larger number of bots in Syria, Bulgaria and United States; the other bots might be the result of side effects.
The infected Android versions
An interesting fact is that more than half of the infected users is using Android 6 or higher, indicating that most users probably still receive the latest security updates.
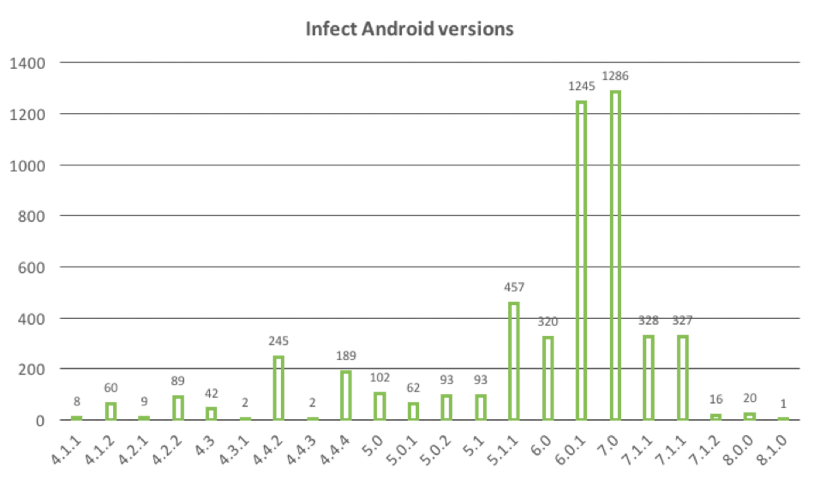
Please note however that, till now, Android banking malware haven’t use platform exploits (which can be patched) to bypass security measures but abuse the security shortcomings of the Android ecosystem to perform malicious actions such as showing phishing overlays and intercepting SMS messages. Most, if not all, of these shortcomings are difficult to “fix” because they significantly reduce the usability of the Android platform.
Overlay targets:
biz.mobinex.android.apps.cep_sifrematik com.akbank.android.apps.akbank_direkt com.akbank.android.apps.akbank_direkt_tablet com.akbank.softotp com.finansbank.mobile.cepsube com.garanti.cepbank com.garanti.cepsubesi com.htsu.hsbcpersonalbanking com.ingbanktr.ingmobil com.intertech.mobilemoneytransfer.activity com.kuveytturk.mobil com.magiclick.odeabank com.pozitron.albarakaturk com.pozitron.iscep com.pozitron.vakifbank com.softtech.isbankasi com.teb com.tmob.denizbank com.tmob.tabletdeniz com.tmobtech.halkbank com.vakifbank.mobile com.ykb.android com.ykb.android.mobilonay com.ykb.androidtablet com.ziraat.ziraatmobil com.ziraat.ziraattablet finansbank.enpara tr.com.sekerbilisim.mbank
Conclusion
The use of dropper apps, especially when spread through Google Play, has become a successful MO for almost all Android banking Trojans. In our opinion spreading dropper apps via an app store that users trust has similar impact than a Malvertising campaign on a popular news site. Having these droppers available in a store for a longer period (in this case around a month) results in thousands of infections and significant amounts of financial fraud.
The security community has taught end users to only trust apps they install from Google Play and to verify that the permissions an app asks are matching with the functionalities of the app. The problem however is that these dropper apps do not have any special permissions. We have seen droppers that enable installation of apps from “unknown sources” abusing the functionality of the accessibility service. Therefore, relying on the “unknown sources” setting is also not foolproof.
As platform features such as unknown sources and the accessibility service are too technical for an average user to understand, training users to prevent installation of droppers is a lost battle. This leads us to believe that this is a problem that should be solved upfront, by keeping the app stores clean and not rely on the knowledge of the end user.
This means Google will have to put some efforts, which so far seem to be lacking.
IOC
1) Play Store com.canli.doviz.borsa 686e0a60a8df7ae504eaf0f6e8c4af58a50b5f7ef2e1c64660eab6b475242677 Dropped 6523272efc4e34f0154b4ea53386bd28c66b461918d59fc87b0e6f90f4acc2c8
2) Play Store com.m.k.ataturk 46f5f841e678706b785a2f375c75ffdbf206a69b6657477d8bc8ffb82a73cf02 Dropped 6523272efc4e34f0154b4ea53386bd28c66b461918d59fc87b0e6f90f4acc2c8
3) Play Store com.dovix e0d0650077a08d1f2feb7181b8376af24f8ef8a36c006d897aea5e710cb1b152 Dropped 2d78ae6c68b5eb5ad6f79025be917acf3e9c9ad07b5a5b9e2cfd6141c86db0d5
Special thanks to Nikolaos Chrysaidos from Avast Software (@virgdroid) who helped us locate additional IOC of this specific Google Play distribution campaign.