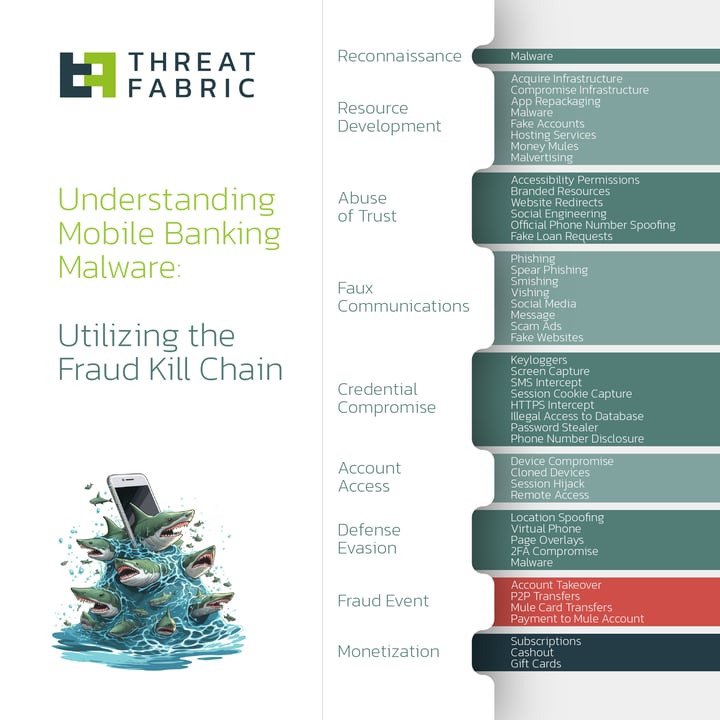
Mobile Banking Malware vs Fraud Kill Chain
27 February 2024

Jump to
This blog is the first of a series, where we will offer the tools to check your fraud detection capabilities for readiness on the most prolific fraud and scam types.
From Malware to Romance Fraud, we’ll analyze TTPs, Kill Chain mappings, and detection gaps.
This first episode is about an upcoming trend: Mobile Banking Malware.
The Problem
Mobile Banking Malware is on the rise. In 2023 ThreatFabric spotted 75 families, of which 26 had Device TakeOver capabilities.
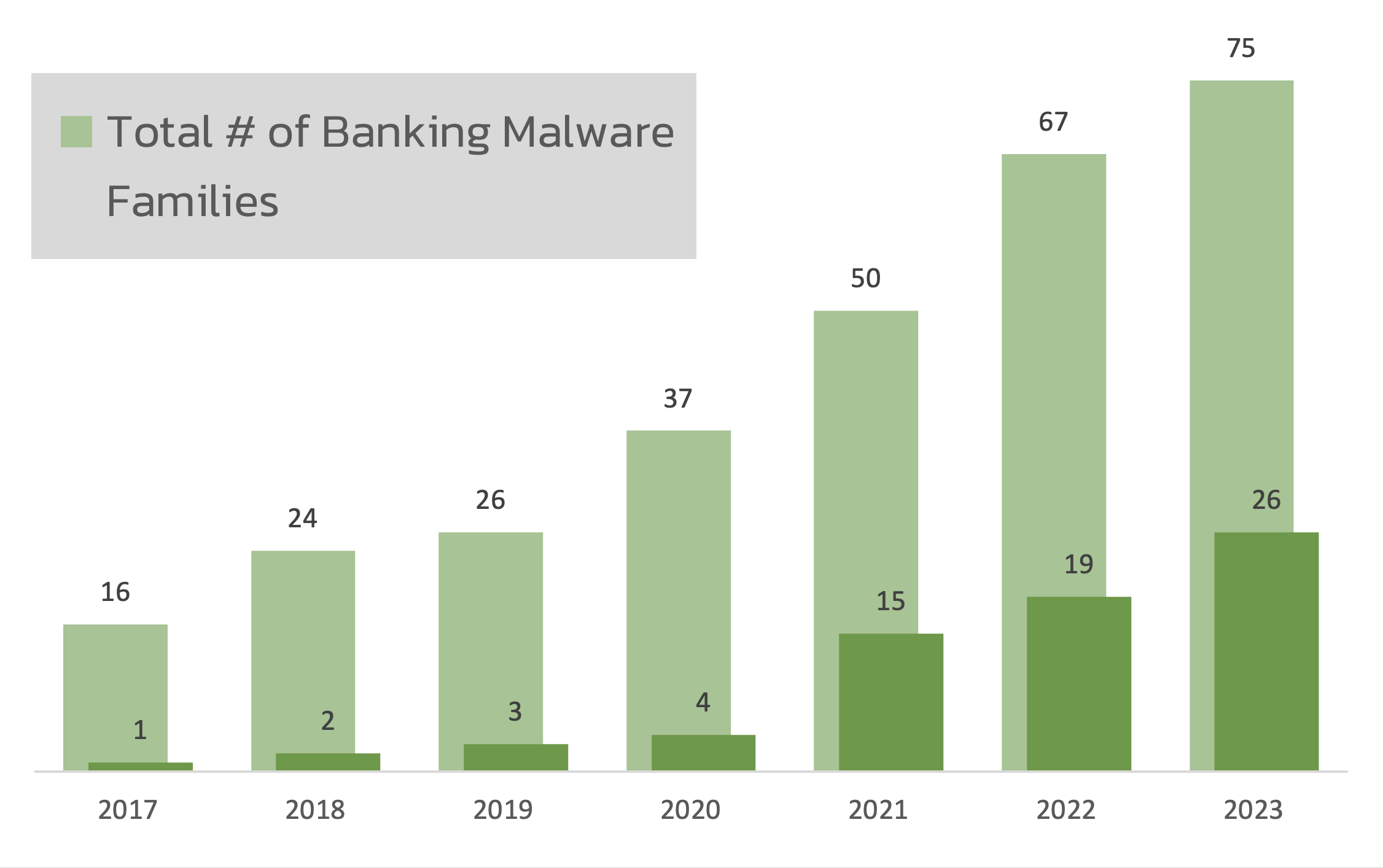
Most of these malwares are delivered through official app stores. They involve a variety of tricks to steal information, and credentials, give Remote Access, or even Automate Transaction Stealing (ATS). One of the most prolific tools used is Anatsa.
> View our recent research article on Anatsa
Detecting Mobile Banking Malware
With the right tools, anti-fraud teams should be able to pick up the tell-tale signs of these attacks. The Fraud Kill Chain is a useful tool to identify detection opportunities and gaps.
Mobile Banking Malware vs Fraud Kill Chain
We can see a plethora of TTPs identifying various stages of attacks before, during, and after. This means there is a lot of opportunity for detection, but it requires sensors and processes in digital channels.
Detection Gaps and Opportunities
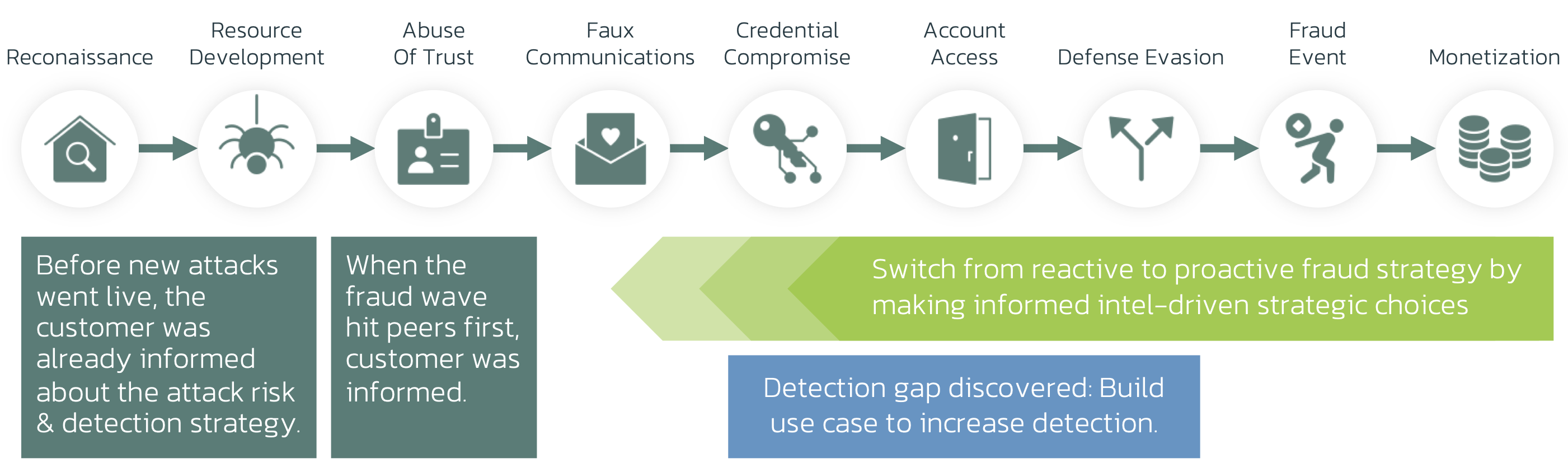
Gap 1: Mobile Visibility
Our research reveals a significant Detection Gap: many organizations struggle with insufficient visibility into Mobile Channels, and some face similar challenges with Web Channels. Implementing effective sensors across these platforms can substantially elevate an organization's capability to detect threats proactively.
Gap 2. User Session Visibility
The second most common gap is a lack of user journey visibility. A lot of tell-tale signs occur between App start and transaction signing: Credential Compromise, Account Access, and Defense Evasion.
Gap 3. Device Risk
The third most common detection gap is visibility on device risk. As the malware executes, it will exhibit tell-tale signs like misuse of accessibility permissions, use of screen overlays, sideload malicious code or bypassing authentication.
Conclusion and Takeaways
As cybercriminals evolve their mobile malware capabilities, anti-fraud teams are to perform the following checks:
- Check your detection processes for mobile visibility, user session visibility, and device risk visibility.
- Use the Fraud Kill Chain mapping to identify specific issues in your attack chain.
- Consider adding detection technology if you identify gaps.
- Stay up to date with the threat evolution with mobile threat intelligence
Detection Readiness Workshop
ThreatFabric helps banks and financials globally perform these analyses. If you’re interested in a detection readiness workshop, please contact us using the link below.